Virtually all industries and organizations can fall victim to fraud, be it financial fraud, insurance fraud, identity theft, or other types of criminality or wrongdoing. Globally, organizations lose up to 5% of revenue to fraud each year according to data from the Association of Certified Fraud Examiners (ACFE). Fraud detection systems can flag suspicious activity - but that’s only the beginning.
When a detection system flags a customer, transaction, or behavior as suspicious, a fraud investigation helps analysts determine if it’s an actual fraud incident. The process also lets them understand if the case is isolated or part of a larger fraud scheme. A single fraudulent transaction may be evidence of a criminal ring, or the suspicious behavior indicative of a wider scam.
In this article, we’ll look at the typical steps of a fraud investigation. Data has also become essential in understanding the behaviors, transactions, etc. that make up a fraud case. We’ll take a close look at the role of data and analytics in fraud investigations, and how you can make the most of innovative tools and technologies for more efficient investigations.
A fraud investigation is a structured inquiry process to detect, document, and build evidence of deceptive activities that result in financial or other material losses. Fraud investigations often begin when an organization identifies suspicious patterns, receives notifications of potential wrongdoing, or detects anomalies through automated monitoring systems. These investigations may look into anything from internal embezzlement and employee theft to external schemes like identity theft, insurance fraud, credit card fraud, benefits fraud, and cybercrime targeting the organization or its customers.
The main objectives of a fraud investigation are to determine whether fraud has occurred, identify who is responsible, quantify the damages, recover lost assets when possible, and gather evidence to support legal proceedings or other actions.
Fraud investigations may rely on specialized techniques like forensic accounting, data analytics, digital forensics, and interviews to uncover fraudulent activities that are often deliberately concealed by bad actors. For businesses and public agencies, conducting thorough and legally compliant fraud investigations is essential not only for recovering lost assets but also for maintaining operational integrity, protecting customers, and staying compliant with regulations.
Fraud investigations can of course vary according to the industry and the fraud typology. But many investigation processes will follow the same general flow. Let’s look at the main steps in a typical investigation of financial fraud.
1- Collect Information
The first step is to gather all the information you have on the case, including transaction records, statements, and any other relevant data. This information can be obtained from various sources, including the victim, the bank's internal systems, and external sources like law enforcement databases.
2- Identify the Fraud
Once you have collected all the relevant information, you need to determine if a fraud has actually occurred. This involves identifying any suspicious activities, unusual patterns, or discrepancies in the data.
3- Secure Evidence
Once you have identified the fraud, you need to secure all the evidence related to the fraud. This includes preserving records of transactions, emails, and other relevant documents that could serve as evidence in the investigation.
4- Conduct Interviews
Next, you need to interview the parties involved, including the victim, the suspect, and any other witnesses. This will help you to gain a better understanding of the circumstances leading to the fraud and to gather additional evidence.
5- Analyze the Data
Analyzing the data involves using analytical tools to identify any trends or patterns in the data. This will help you to uncover any hidden connections or relationships that may exist between different transactions or parties involved. In this step, you can also determine whether the fraudulent behavior is an isolated incident or part of a larger fraud ring.
6- Report Findings
Once you have completed your investigation, you need to report your findings to the appropriate authorities, such as law enforcement, the victim, or senior management. A fraud report should include a summary of the investigation, the evidence gathered, and any recommendations for preventing future fraud.
7- Take Action
Finally, the organization that has been impacted needs to take appropriate action based on the findings of the investigation. This could include freezing the account, terminating the suspect's access to the account, or filing a police report. The organization should also take steps to prevent future fraud by implementing stronger security measures and monitoring systems.
The length of a fraud investigation depends on what the process uncovers. If no fraud is identified, the case can be closed quickly. But when suspicious activity is confirmed, the investigation becomes more complex.
Opportunistic fraud cases can often be resolved in just a few days. However, when the evidence points to a broader scheme—such as an organized fraud ring—the investigation may take months or even years. These cases often involve multiple actors and sophisticated tactics, and may require collaboration with law enforcement to bring the full picture to light.
Gaining a full understanding of any given fraud case requires finding evidence within your data: personal data, transaction data, public data, data about businesses, and more.
Data structure has a major impact on the speed and efficiency of a fraud investigation. Many organizations use manual fraud investigation techniques, which are time-consuming and can miss key information.
Finding the information to understand if wrongdoing has occurred or not is a long process when the data is scattered across different tabs or stored in isolated silos. Verifying the identity of individuals connected via financial transactions, for example, requires opening a first tab with the person’s transactions and recipients. Then you need to repeat the process for each recipient.
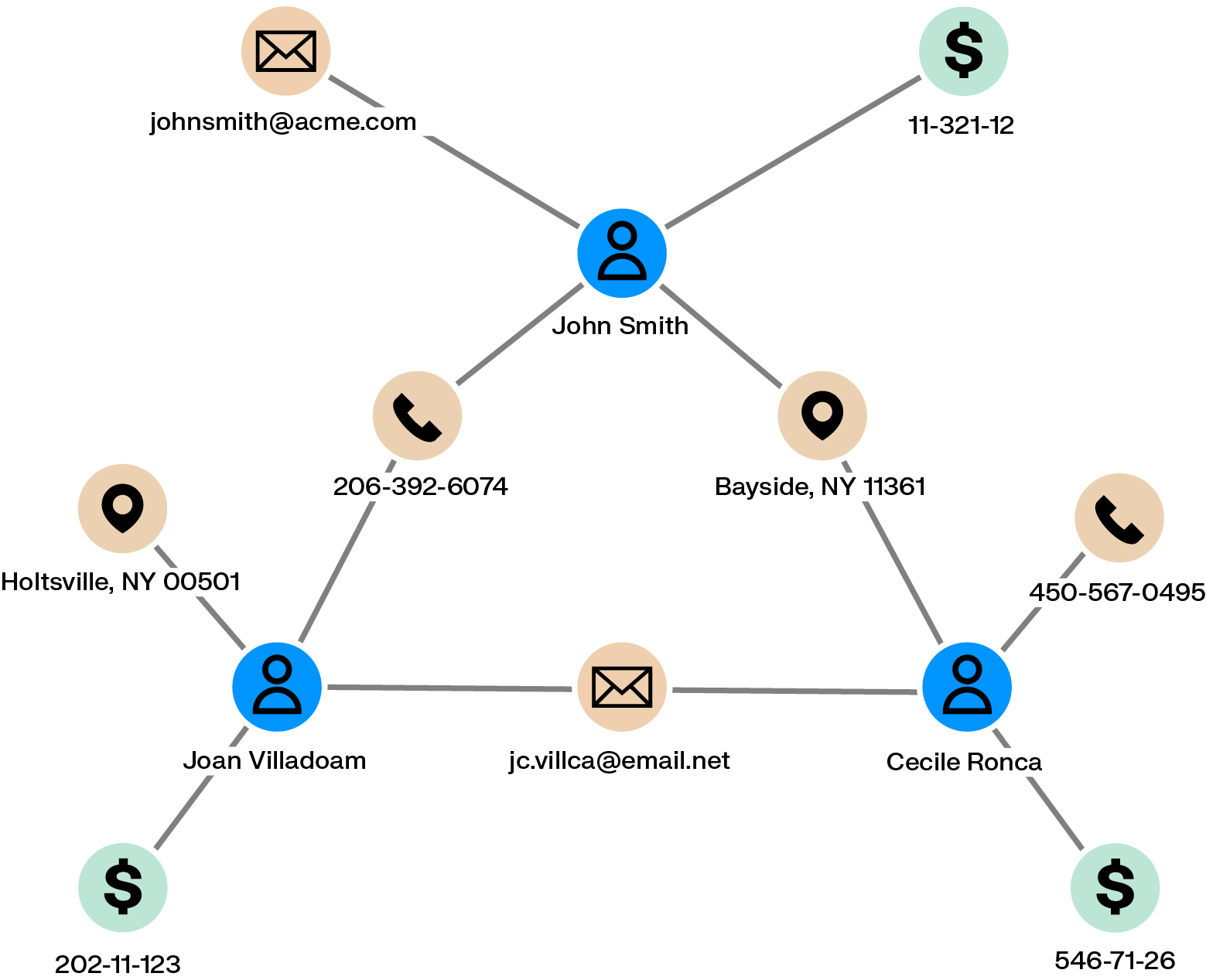
In fraud investigations, it’s not just about identifying individuals—but understanding how they’re connected. In a graph data model, relationships are as important as individual data points. When working with a graph, data is presented as nodes (such as people, accounts, or transactions) and edges (the relationships between them), making it easier to explore complex networks and uncover hidden risks.
With this approach, investigators can dynamically visualize a client’s connections—through addresses, phone numbers, emails, or shared transactions—making it much faster to identify potential accomplices or suspicious behavior.
Graph algorithms quickly answer many of the questions that are relevant to fraud investigations. Is one of your clients indirectly connected to a politically exposed person? A pathfinding algorithm will reveal if they are. Is a given fraudster actually part of a bigger network? A community detection algorithm can help you understand if they are, and who their accomplices might be.
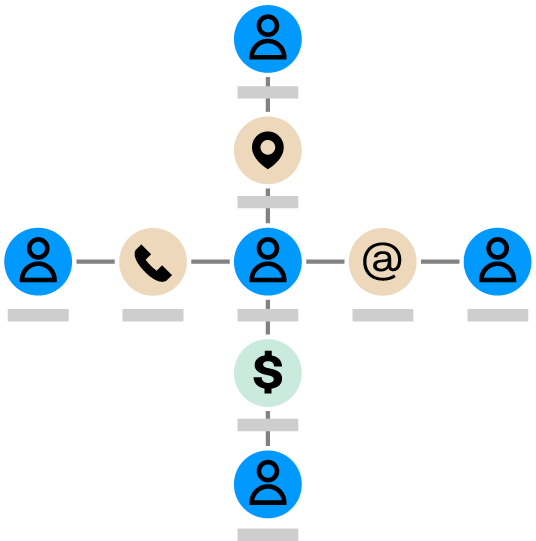
Fraud can take many shapes. Here are four types, and how graph analytics can help untangle the connections behind each scheme.
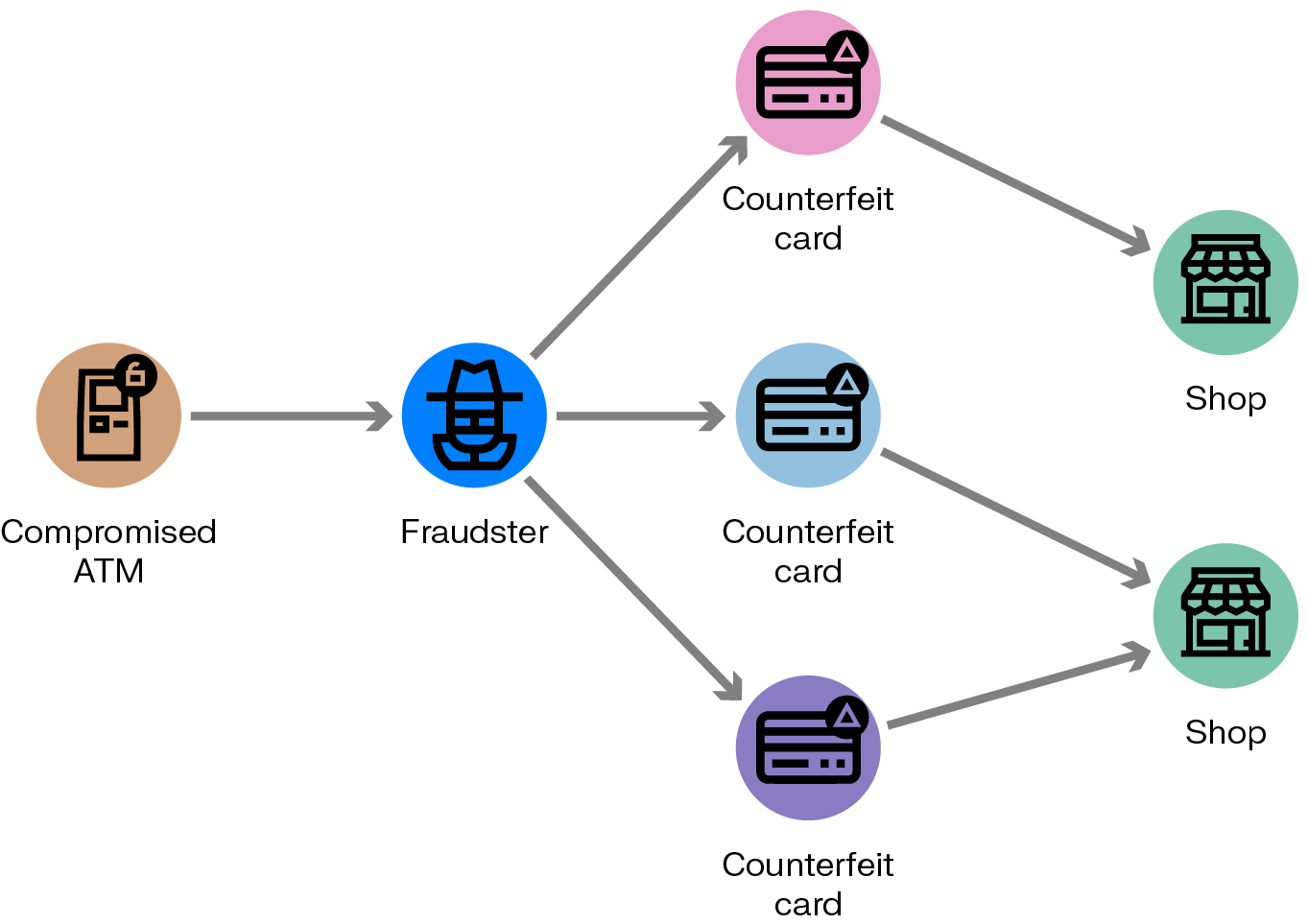
1- Credit and debit card fraud
Fraudsters use stolen card data to make unauthorized purchases or resell credentials. Graph analytics reveals patterns like multiple cards linked to the same IP, shipping address, or account—surfacing potential fraud rings behind isolated transactions.
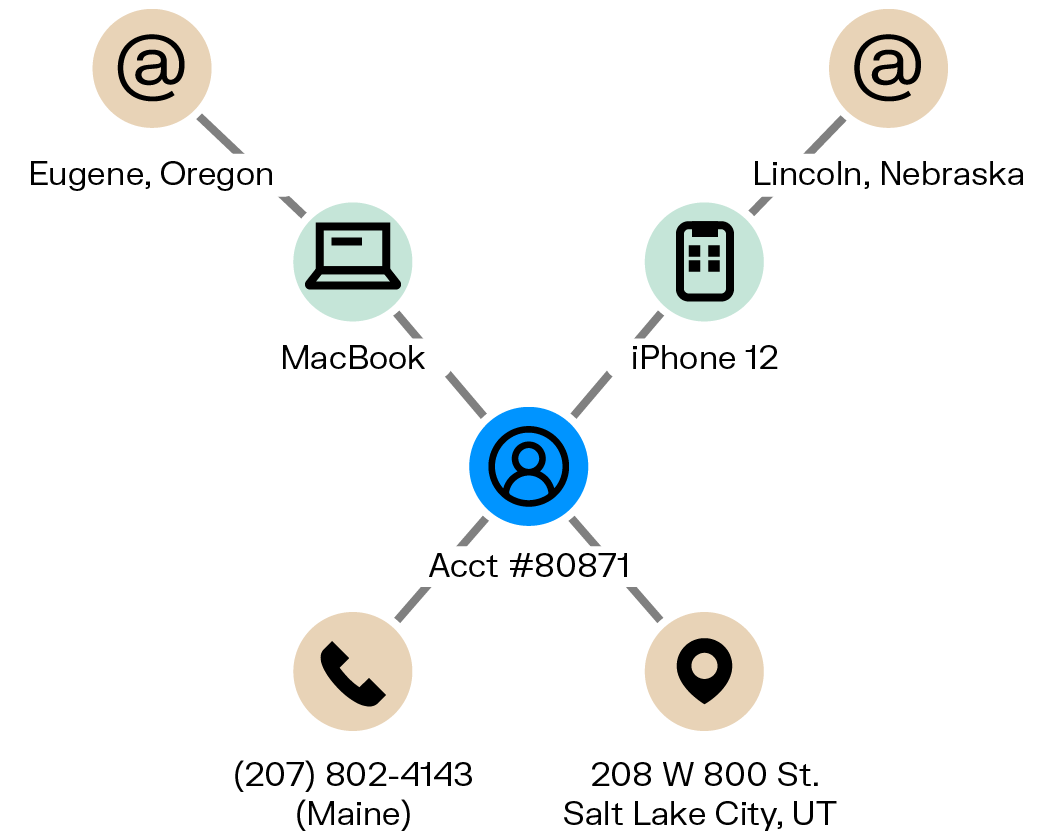
2- Account takeover (ATO) fraud
In ATO fraud, criminals gain unauthorized access to user accounts and make changes or transactions. Graphs can link unusual logins, device fingerprints, or password resets across accounts—uncovering coordinated takeovers and shared infrastructure.
3- Cryptocurrency fraud
Because crypto transactions are hard to reverse and often anonymous, tracing them is tricky. Graphs help visualize flows between wallets, exchanges, and users—surfacing suspicious clusters and hidden paths that may indicate laundering or scams.
4- Synthetic identity fraud
This occurs when criminals mix real and fake data to create new identities. Graph analytics connect shared data points—like emails, addresses, or phone numbers—to flag synthetic profiles and uncover potential fraud rings operating behind them.
Doing a thorough fraud investigation that gives you a complete picture of what happened helps inform risk. And better understanding fraud risk means better fraud prevention.
Fraud investigation is part of a virtuous circle. The intelligence gathered from an investigation helps identify new patterns and criminal methodologies. And that information can in turn be used to create countermeasures to prevent the fraud from occurring again. It can also help scale fraud detection, particularly when using a graph analytics solution, in which it’s easy to create new alerts to flag new types of suspicious activity.

