Fraud is defined by its deceptive nature, aiming to gain personal or financial advantages unlawfully or unfairly. As technology advances, fraud schemes have become increasingly complex. Digital transformation offers criminals a wider array of possibilities to exploit for their own gain.
This presents a growing challenge for all kinds of organizations, including banks and insurance companies, as well as individuals who may fall victim to these crimes. To avoid being one of those victims, understanding the distinctions between first-party, second-party, and third-party fraud is crucial in fighting against many of these schemes.
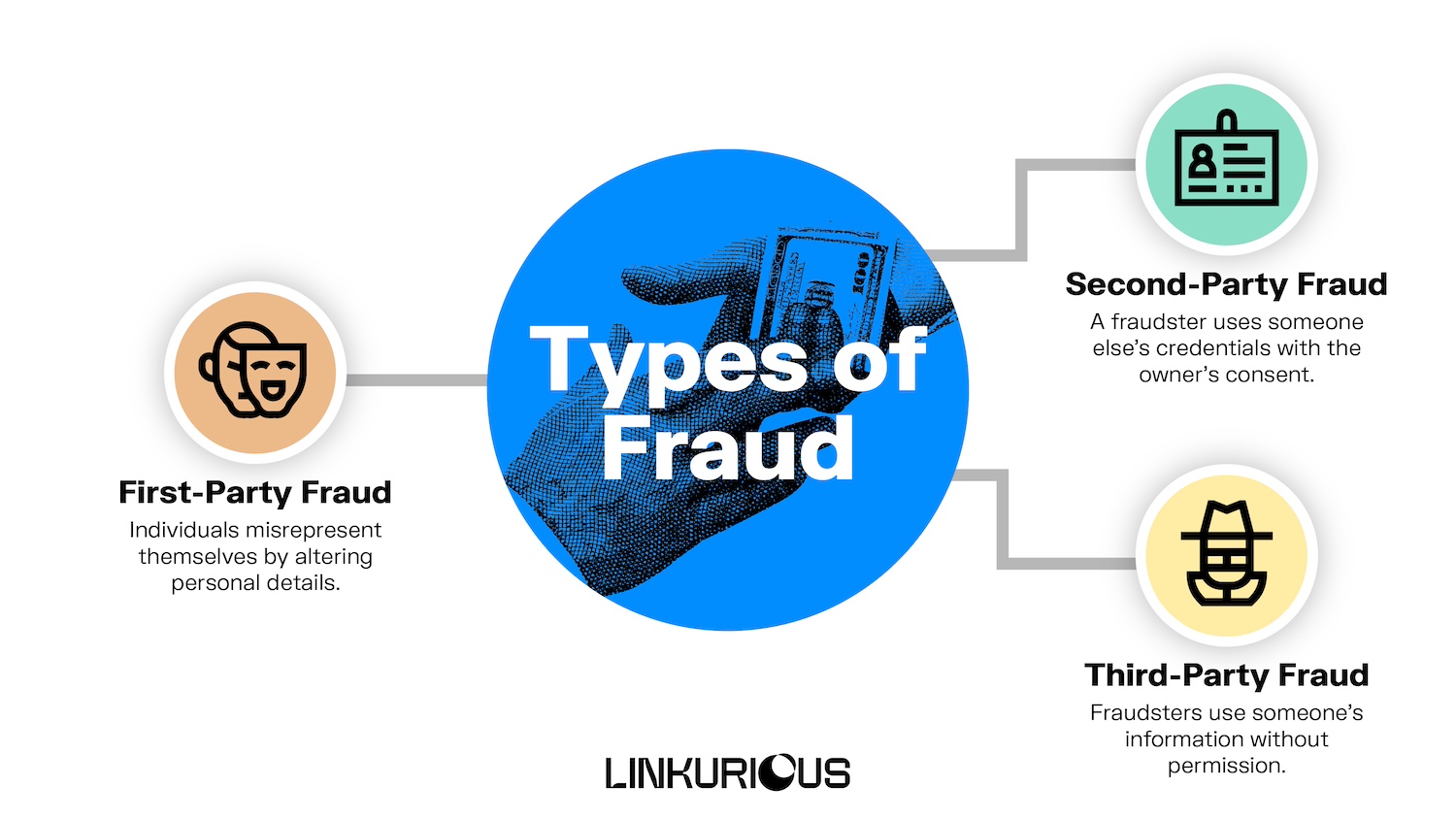
If you've come across these terms before, you might wonder how these three different types of fraud work. Here’s a quick breakdown of what these different fraud labels refer to.
- First-Party Fraud: This involves individuals misrepresenting their own identity by altering personal details or creating synthetic identities, often to obtain loans or credit cards.
- Second-Party Fraud: This is when an individual uses stolen or borrowed credentials or information with the owner's permission, such as using a family member's identity for transactions they may or may not be aware of.
- Third-Party Fraud: This occurs when using someone's information without their consent, often through hacking, to commit fraudulent activities or gain unauthorized access to resources.
Second-party fraud is when someone - a family member, friend, or even a stranger - lets a fraudster use their identity or credentials to make transactions, open accounts, etc. In this way, the fraudster hides behind a legitimate looking identity, making these fraud schemes very hard to track down. The person who authorized the use of their identity may or may not be aware that shady activity is going on.
This type of fraud often targets young, elderly, or otherwise vulnerable victims, who may agree to let a fraudster use their accounts or credentials in exchange for a bit of money.
Here are a few examples of common second-party fraud schemes:
- Family Member Identity Theft: A common scenario is when a family member, with the victim's consent, uses their financial information to obtain a loan or credit card. For instance, a grandson might use his grandfather's personal details to apply for a credit card, with the grandfather's knowledge but without his understanding of the potential consequences, such as unauthorized purchases and debts in his name.
- Money Muling: In this common scam, an individual allows someone else to use their bank account to facilitate illicit financial transactions, such as money laundering. The account holders may be promised a portion of the funds transferred as compensation for their cooperation. They might not fully comprehend the illegal nature of the activities being conducted, making them unwitting accomplices in the fraud scheme.
- Scammer transfers: Similar to money muling but even more subtle. In this scheme, the victim receives a transfer, for example of 5,000 euros, and later a message requesting the return of the amount but to a different account. The victim agrees and carries out the procedure, unknowingly becoming involved in a money laundering scheme.
If the possibilities for second-party fraud are increasingly complex with the use of technology, fraud fighters should also look for more robust solutions that help prevent these crimes. By examining the intricate relationships and connections within financial transactions, graph technology can identify suspicious patterns indicative of second-party fraud.
Graph technology can uncover instances where legitimate account holders are authorizing transactions that deviate significantly from their typical behavior, signaling potential coercion or manipulation. Additionally, graph analytics can detect anomalies in transaction flows, such as sudden increases in the volume or frequency of transfers between related accounts. And because graph visualization is perfectly suited to examining relationships, you can quickly see which accounts are connected, making it easier to track down schemes like money muling.

By integrating graph analytics into fraud detection systems, banks and financial institutions can proactively identify and mitigate second-party fraud, thereby safeguarding both their assets and their customers' interests.
Learn more about using graph technology to detect and investigate fraud schemes in our dedicated ebook.
