Fraud is on the rise globally: according to a 2022 PwC study, 51% of surveyed organizations experience fraud in the previous two years, the highest level in 20 years of research. There are countless types of fraud schemes - countless ways a fraudster can scam a person or a business out of money or other assets. This article takes a look at some of the most common ones - with some visualizations to show how they work.
A fraud scheme is one of the multitude of ways scammers illegally procure funds from a person or business. Fraud schemes are a type of theft.
In the case of many common fraud schemes, the scam can be internal, external, or collusion. Internal fraud is when the crime is committed by someone within an organization - an employee depositing checks to their own account for example. External fraud is when a business is the victim of someone outside their organization - like a hacker sending spear phishing emails. And collusion is when the two work together, which could look like a corrupt banker approving bad loans in a mortgage fraud scheme.
Fraud schemes can also be categorized as first-party fraud, second-party, or third-party fraud.
- First-party fraud is when a fraudster purposely misrepresents their identity by using a synthetic or stolen identity.
- Second party fraud is when a fraudster uses stolen or borrowed credentials to commit fraud, with the owner’s permission.
- Third-party fraud is when someone's personal information is used without consent so a third party can illegally or unfairly gain access to resources, credit, or products.
By nature, fraud is constantly evolving. New scams and patterns evolve as new opportunities emerge and fraudsters find ways around detection and prevention measures, requiring sophisticated fraud analytics to investigate.
Still, there are known types of fraudulent behavior, and many types of fraud occur again and again, across different geographies and types of businesses.
While not an exhaustive list, this article covers some common fraud schemes that regularly impact businesses, financial institutions, and individuals.
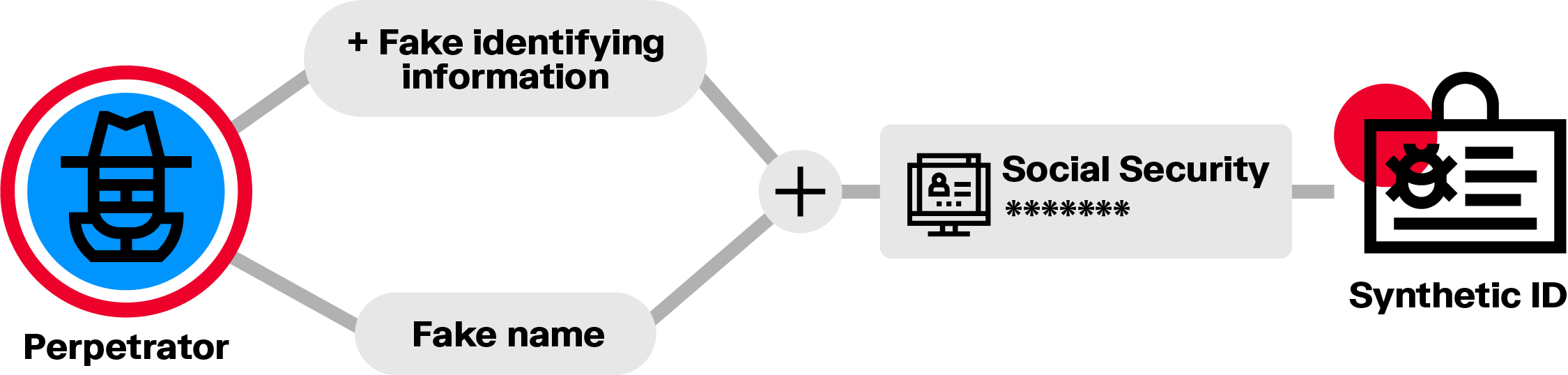
One way a fraudster may try to cover their tracks is by creating a fake identity to open a bank account for example. A synthetic identity is a false identity mixing real and fake information, such as a real social security number and phone number, and a fake name. These attributes do not belong to a single real person. It’s one of the fastest growing types of financial crime in the US according to estimates by McKinsey, and poses a problem globally. It can be a particularly difficult type of fraud to detect.
All companies spend money to operate, creating an opportunity for fraud networks to take advantage of weak controls in procurement processes. A rogue employee might coordinate with a supplier to defraud the company, for example. Or an ill-intentioned HR manager might keep former employees in the company’s system and redirect their salaries for personal gain. There’s potential for substantial money losses in cases of procurement fraud.
Online fraud schemes like phishing attacks are increasingly common. The cyber criminals behind these schemes will impersonate banks via email, text message or phone call to harvest the credentials of their victims. Once they have access to bank accounts, they empty them. Account takeover fraud has become more widespread as more and more consumers turn to online banking. It’s a major threat to brand equity for financial institutions.
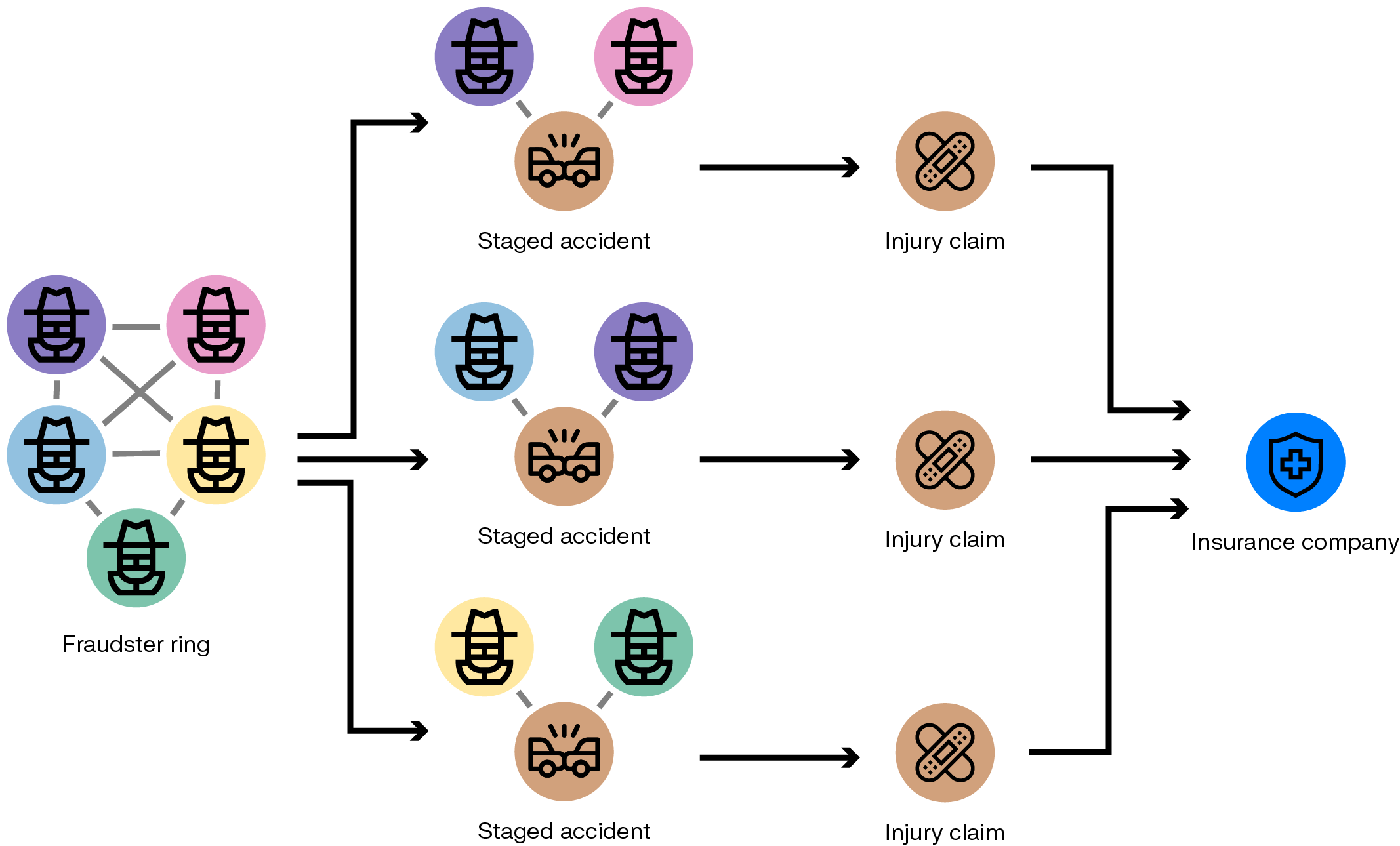
Generating fake insurance claims can be a way for fraudsters to make money. Let’s look at the example of a fake car accident scam. A scammer can take a car insurance policy, then claim a refund on a non existing car accident. A car repair shop acting as an accomplice can generate invoices for non-existent repairs to trigger payment from the insurance company.
Some fraud networks abuse the system of government benefits, like unemployment. It’s possible, for example, to use a legitimate employment document and tweak it to claim unemployment benefits on behalf of multiple persons. Those involved may keep a percentage of the stolen money and share the rest with the scam’s organizers.
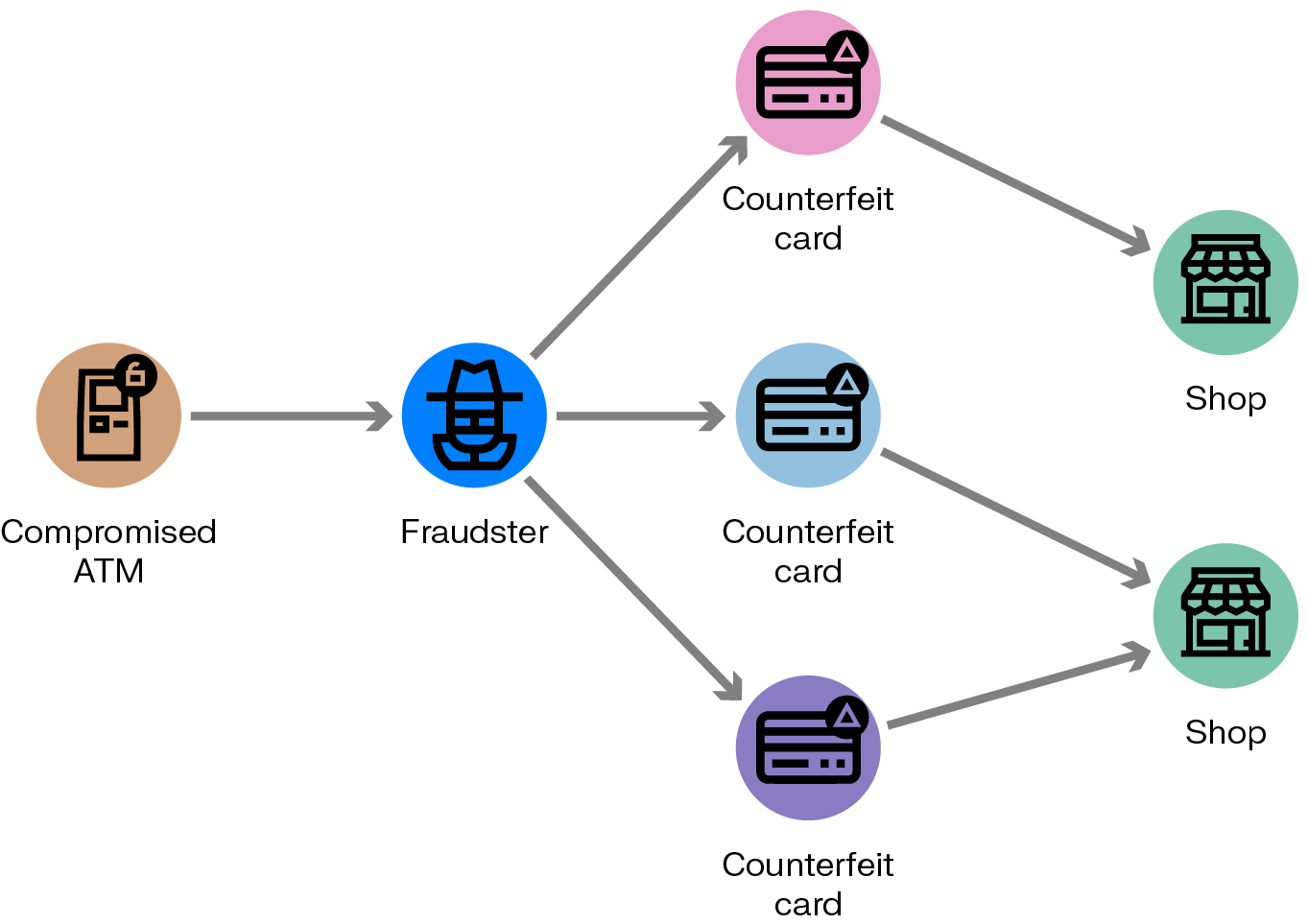
A credit card skimming device copies a credit card when it’s used to pay at a card reader at an ATM, gas pump, or other point of sale. The device owner can then use this information to make fraudulent transactions, such as online purchases.
Corrupt practitioners can receive fraudulent reimbursement by billing for services they haven’t provided. Institutions such as Medicare pay those bills. It’s particularly hard to stop this when the practitioners claim those services were performed on older patients who may be more vulnerable and therefore less likely to report fraudulent behavior.
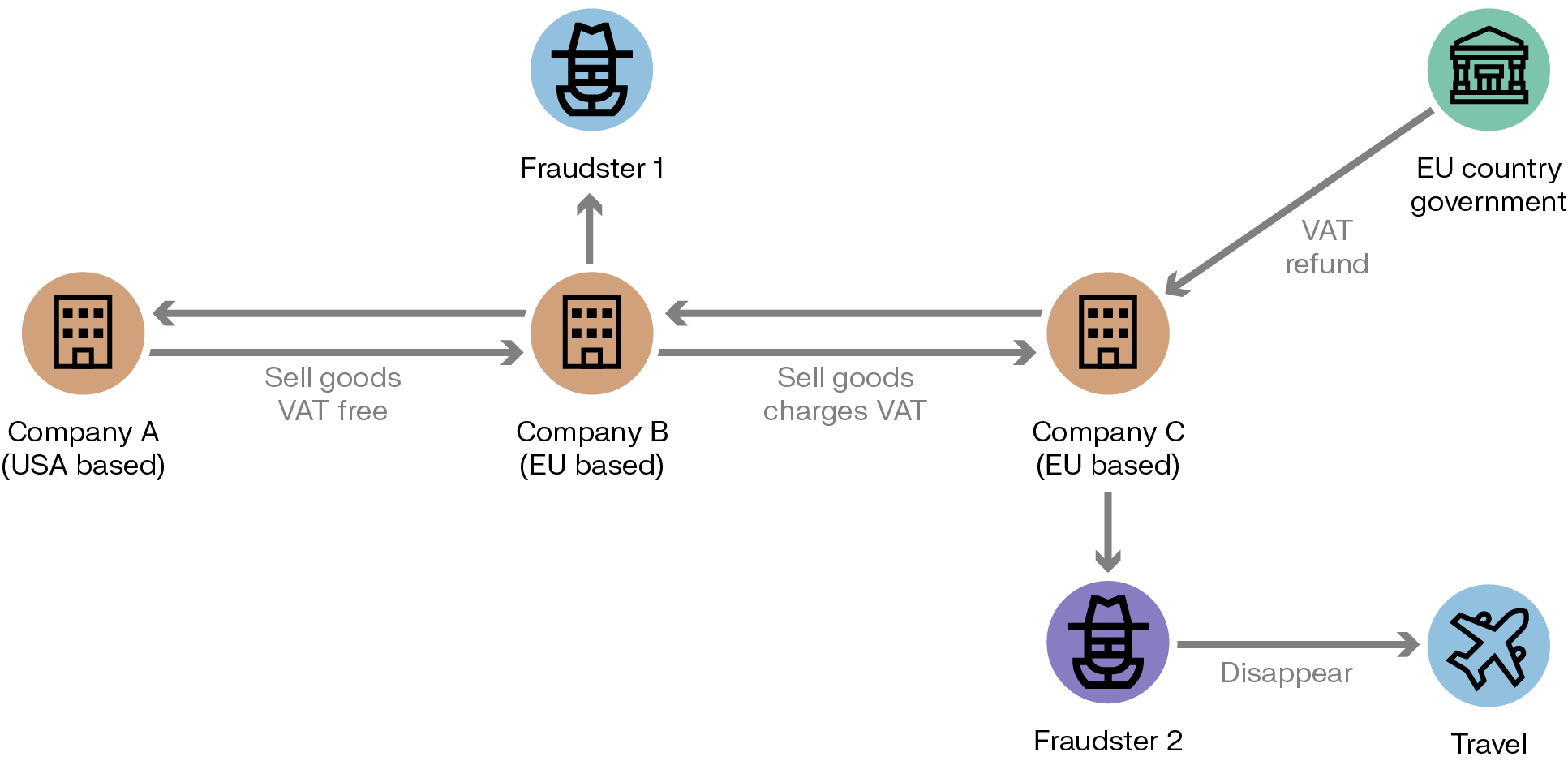
VAT fraud is also known as carousel fraud. By arranging a series of international transactions between cooperating companies, it’s possible to claim a VAT refund without ever paying the VAT in the first place. Operating the scheme requires a company that can charge the VAT tax to a client and then disappear without ever transferring the money to the tax authority. Fraudsters must therefore take over or create multiple companies.
Cyber fraud is a broad category of fraud that includes many types of financial crime that happen online: malware, trojan horses, viruses, phishing emails, and more. It could be someone impersonating the CEO of your company to gain account access, or hackers holding a computer system for ransom. Cyber fraud is on the rise as more interactions and transactions move online.
To inflate a bonus or retain a job, someone might misrepresent the financial state of a business, overstating assets, revenues, or profits, or understating liabilities. Financial statement fraud rarely results in personal gain for the fraudster. This type of scheme belongs to the broad category of internal fraud.
New technology like graph analytics and visualization are powerful assets in both detecting and investigating complex fraud schemes. Layered onto existing systems, it can help detect more fraud, faster, and accelerate investigation time.
To take a deeper dive into how this technology can improve upon your anti-fraud tech stack, take a look at our e-book: Outsmarting fraudsters with next-generation technology.


