Cyber security threats have only increased in recent years, as the increase in remote work and services has accelerated digital transformation. By 2025, the global cost of cybercrime is projected to reach $10.5 trillion USD, up from $3 trillion USD in 2015 (1).
Preventing and analyzing threats is as challenging as it is essential. Cyber security threat analysis involves pulling together data from multiple platforms and sources, and analyzing the connections within at scale. At the same time, it takes an attacker mere seconds to exploit a vulnerability in a system.
This article looks at how to deal with security information and event management/log management (SIEM/LM) data overflow, and how a graph visualization solution can help more easily identify and investigate cyber security threats. We’ll look at specific examples of how to perform precise real-time and/or post-attack forensics analysis using Linkurious Enterprise graph visualization and analytics software.
SIEM/LM is a type of software solution used to manage security events and logs from various sources, including network devices, servers, and applications. The solution collects, analyzes, and correlates log data in real-time to provide security teams with a comprehensive view of their organization's security posture.
SIEM/LM solutions aim to provide analysts all the necessary information and context they need to determine the nature of an attack, its degree of sophistication and of proliferation inside the network. To efficiently contain security breach damages and react efficiently, analysts need the right information at the right time.
As powerful as many cyber security tools are, it remains challenging for organizations of all sizes to meet their operational, audit, and security needs. As networks become more and more complex, the number of devices to monitor has also significantly increased, along with the amounts of data.
SIEM/LM systems are designed to collect and analyze log data from various sources, including network devices, servers, applications, and endpoints. This data can include system events, application logs, firewall logs, network traffic logs, and more. The goal of this approach is to provide a comprehensive view of an organization's security posture and help detect and respond to security threats.
However, the volume of log data generated by these systems can be overwhelming. In some cases, SIEM/LM systems may generate thousands or even millions of log entries per day, depending on the size and complexity of the organization. This overflow of data can make it challenging for security analysts to effectively analyze their data.
There is a real need to reduce the scale and complexity of the analysis to a more intelligible level in order for analysts to come up with appropriate solutions to improve overall security. Advanced data visualization solutions powered by graph analytics enable just that.
Working with SIEM/LM data centralized into a data lake, graph visualization and analytics can provide data analysts with real added value for their everyday operations as they explore and investigate their data.
Graph analytics involves representing data as a network of nodes (entities) and edges (relationships between entities) and analyzing the connections and patterns in this network to gain insights. It is particularly well adapted for efficiently analyzing large and complex data sets with many connections.
Graph has many applications in the domain of cyber security. Graph analytics can be used to detect anomalous behavior in a network, such as unusual patterns of data access, data exfiltration, or lateral movement, helping flag suspicious activity and identify security threats. Graph can also be used to identify vulnerabilities in a network by analyzing the relationships between different entities and identifying potential attack paths. Analysts can then use that information to prioritize vulnerability remediation efforts and help mitigate cyber security threats before they ever occur.
Adding graph visualization on top of existing technology can further empower security analysts. Visualization considerably reduces the scale and complexity of security analysis. And, visualizing complex networks makes cyber security threats easier to understand and explain, which can empower analysts to react to threats more quickly.
Let’s take a look at how a graph visualization solution like Linkurious Enterprise performs for cyber security threat analysis using a real life SIEM/LM dataset.
This dataset was created using a real life log archive of an enterprise network. Courtesy of the University of Victoria who created and made public the dataset for general research purposes. The dataset is the combination of several existing publicly available malicious and non-malicious SIEM/LM log datasets. The dataset reproduces the day to day usage of an enterprise network. More information on the dataset here.
The PCAP files were generated with Wireshark and we converted it into a CSV file. We then generated several CSV files to model the dataset and import it into Neo4j.
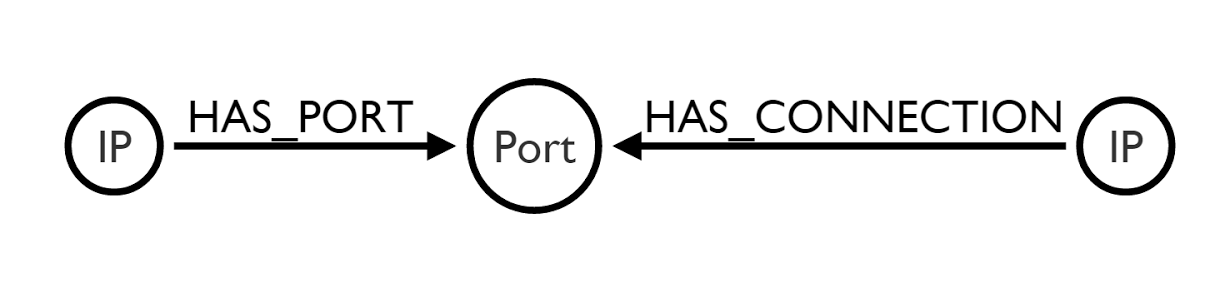
Modelling
We used the following model for the Neo4j database:
Import Script:
cd C:\Users\linkurious\Downloads\neo4j-community-3.0.1-windows\neo4j-community-3.0.1\bin
neo4j-import –USING PERIODIC COMMIT 1000 –skip-bad-relationships –C:\Users\linkurious\Downloads\neo4j-community-3.0.0-RC1-windows\neo4j-community-3.0.0-RC1\bin –nodes nodeip.src.csv –nodes nodeport.csv –relationships Relationshipdst.portip.dst.csv –relationships RelationshipIP.srcdst.port.csv –into C:\The connections were aggregated together with the start date and end date to reduce the number of edges. Creating an edge for each transmitted packet would create super nodes and make the graph very difficult to read. The model we use is very simple, but the modeling can be made to fit very specific use cases depending on what the analyst is looking for.
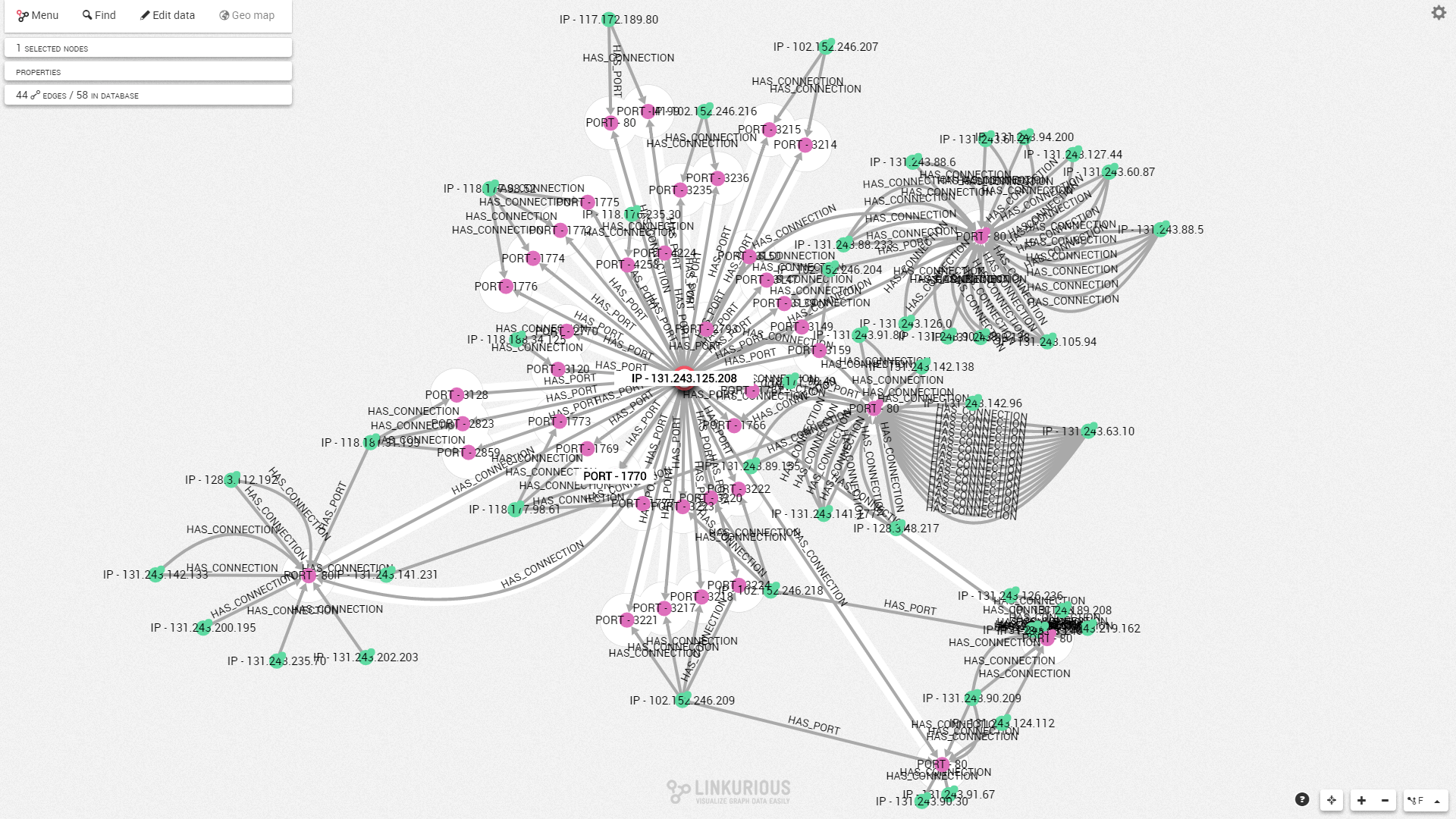
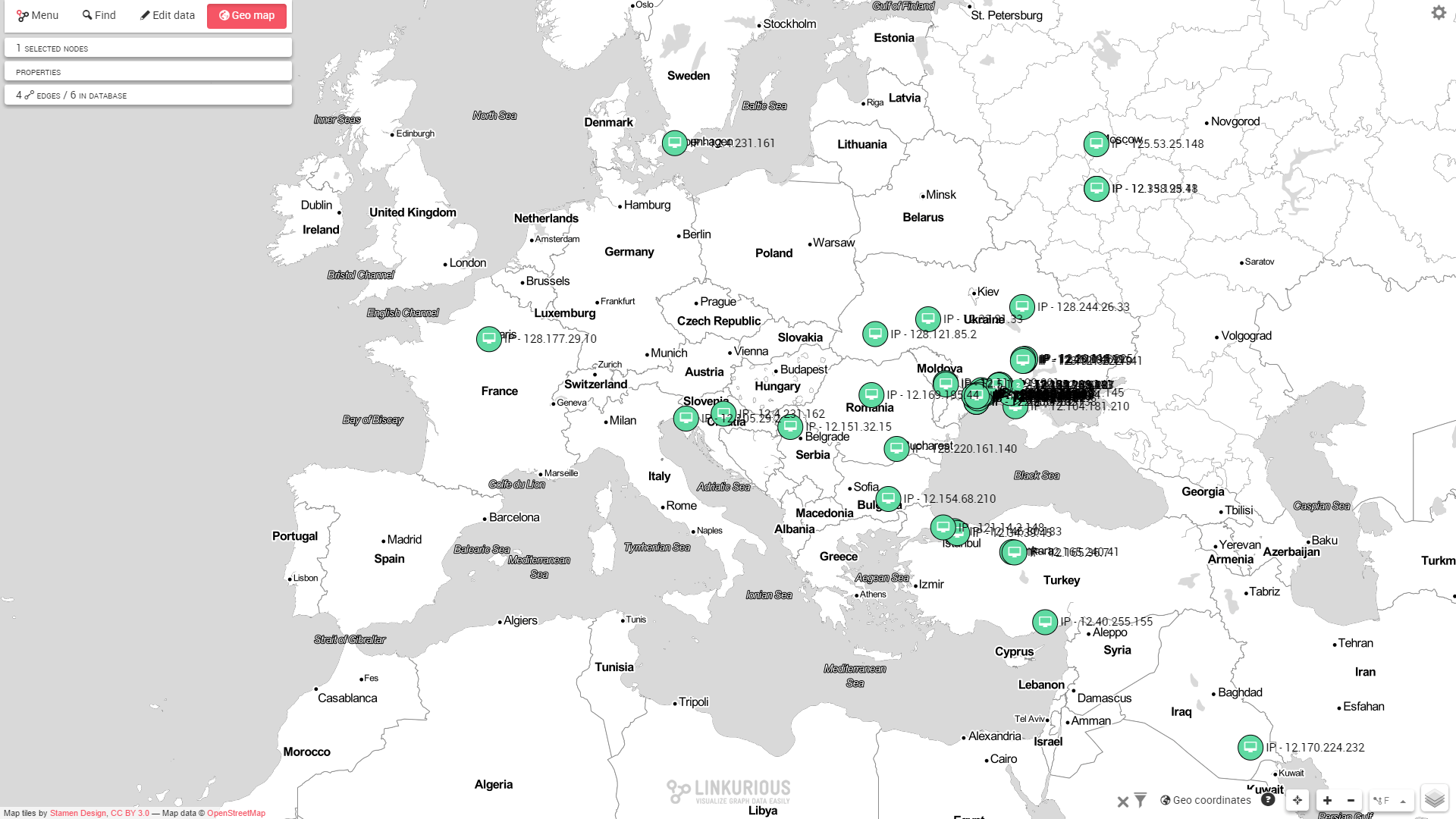
Linkurious enables analysts to visualise data that is otherwise seemingly difficult to conceptualise. Experienced analysts know what “normal” behaviours looks like on the network they manage. This makes it possible for them to set pattern detection algorithms that will pull up abnormal behaviours from the database. For example, the following visualisation shows a “normal” interaction in the network. IP’s interact with a wide variety of different service ports of 131.243.125.208.
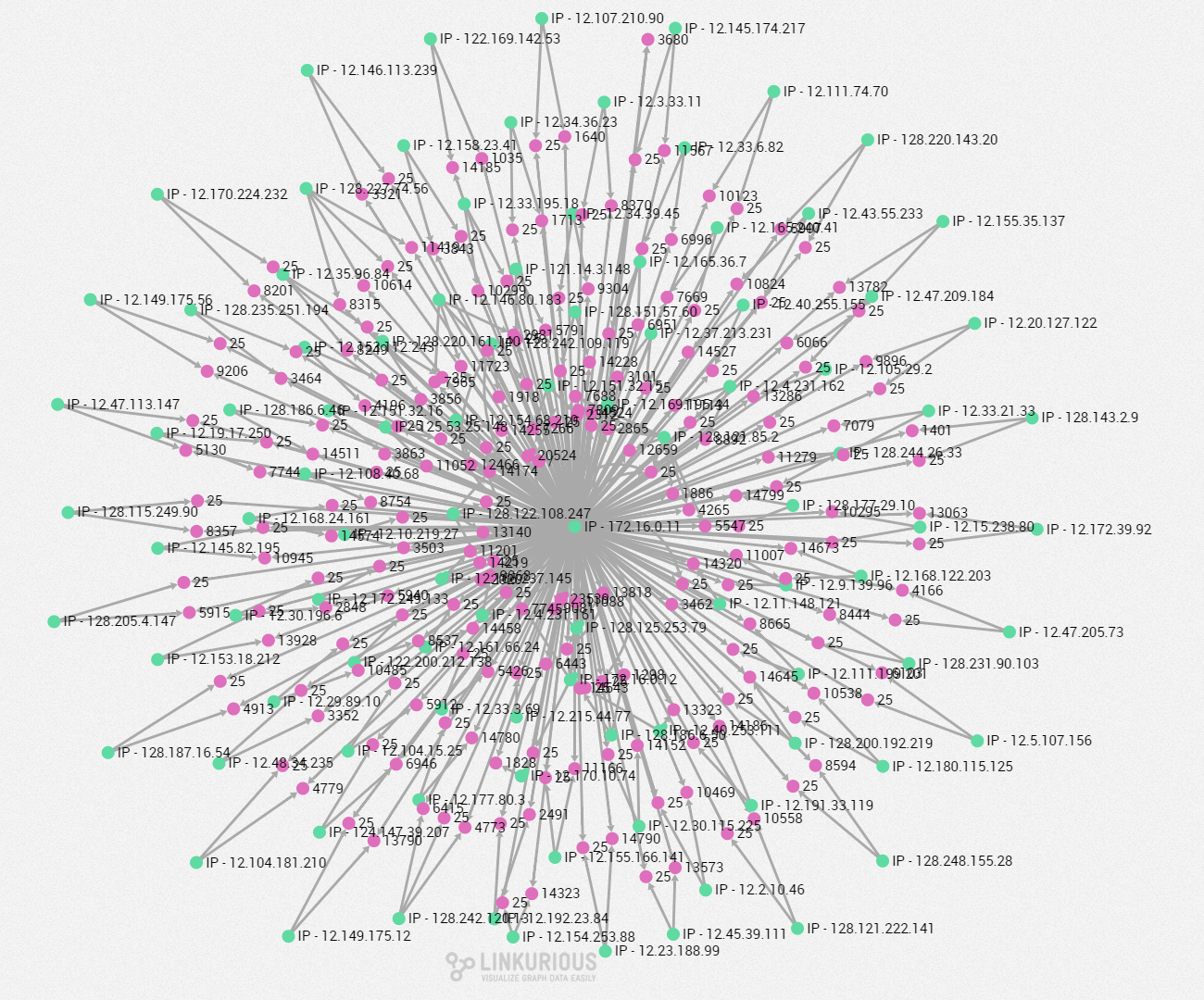
On the other hand, here is an abnormal behaviour pattern. Most of the IPs that connect to “172.16.0.11”use port 25 (SMTP Port) and don’t generate any other traffic than that on any other services. This is suspicious in itself. But the large number of IP’s doing the same operation at the same time seem to indicate a botnet network carrying out a UDP storm attack. These attacks are basically a denial of service attack (DoS).
If a geolocation service fetches the GPS coordinates of the IP addresses, it is possible to visualise them directly on a map. In one click, using Linkurious geospatial visualisation feature, we can see that most of the IPs that are part of the botnet network are in the same region. Most of them come from around Odessa in Ukraine.
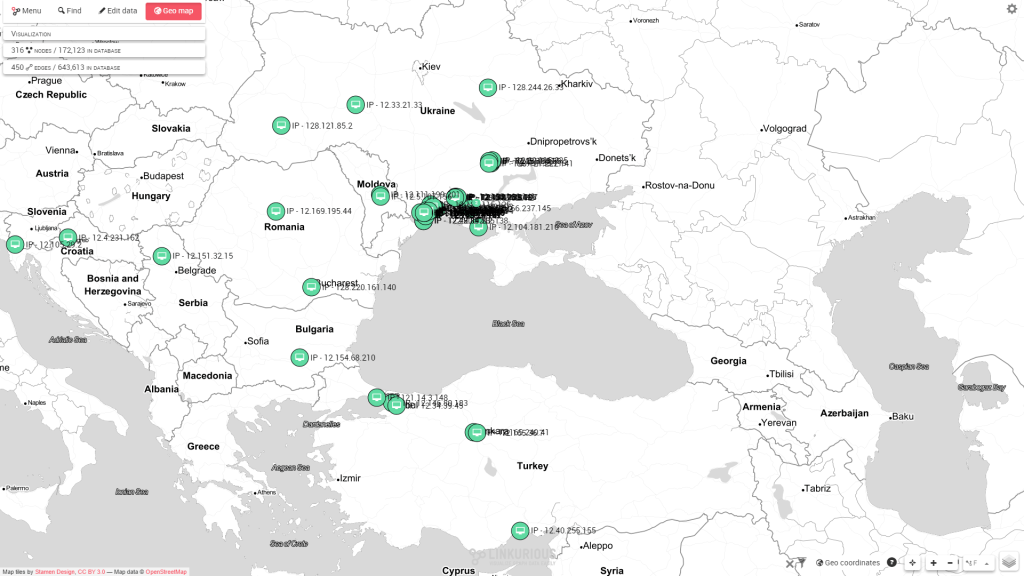
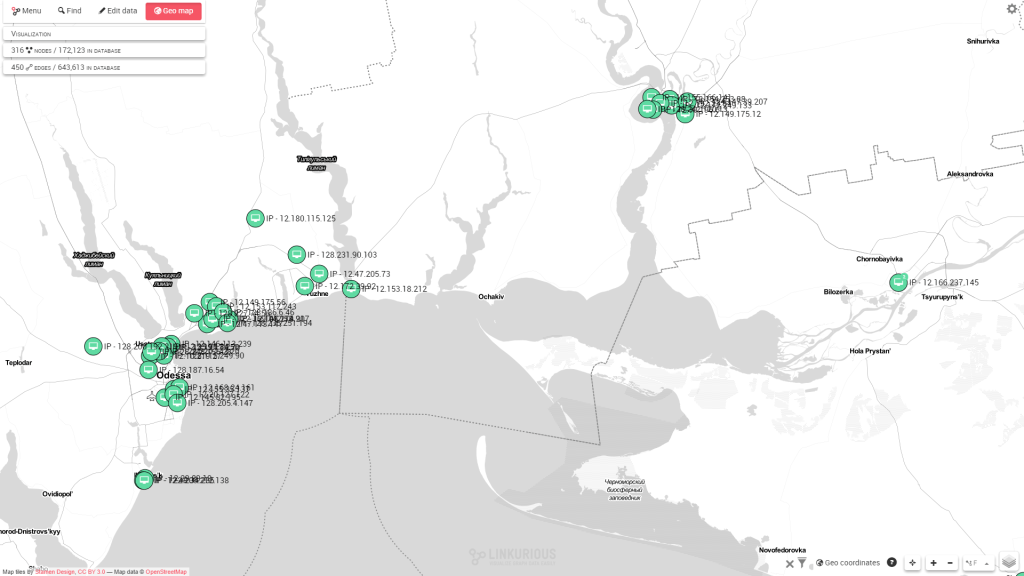
Most of the toxic traffic comes from Ukraine around Odessa
We can then explore the activity of specific IP addresses and see which services were affected by their activity. For example, the address “12.166.237.145” has other links that we haven’t examined yet. Let’s examine it separately and expand it to see all its connections. That way, we see it links to another IP on our network: “172.16.0.12”.
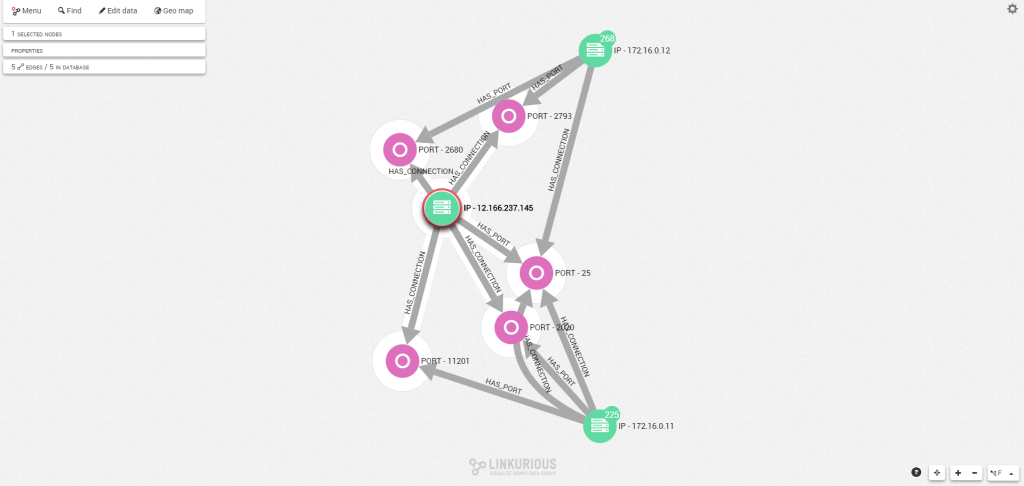
If we expand the IP address “172.16.0.12” to see its connections, we find it is connected to another attack. This means the two are probably linked together and that the network was maybe compromised several times. The attack follows the same pattern as the first SMTP storm attack we just saw.
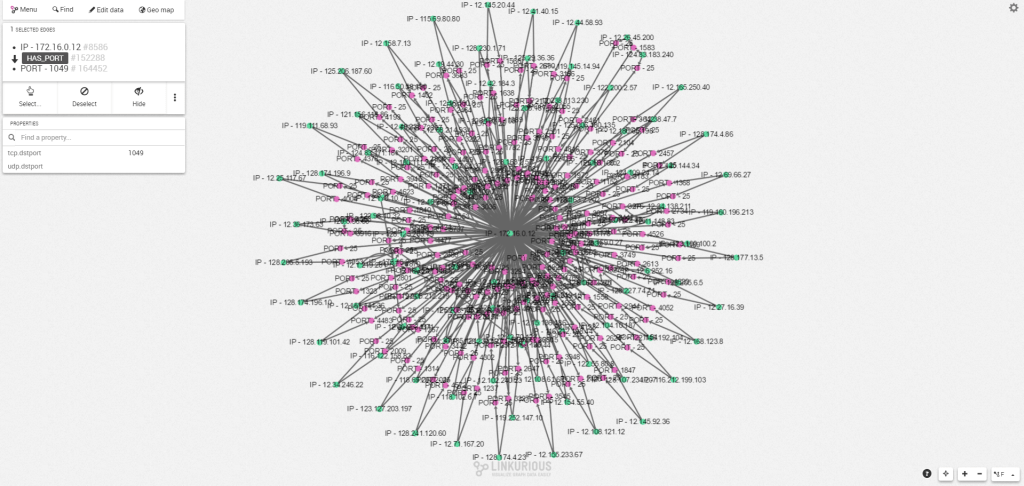
This simple use case shows the great potential graph visualization technology has for cyber security threat analysis. It helps analysts more easily make sense of their connected data and investigate any suspicious behaviors in their network. Graph visualization offers a fast and precise way for analysts to understand any kind of security event. Assessing the degree of sophistication of an attack and reacting accordingly becomes easier than ever before.
Graph technology also enables the automation of a large part of the detection process, allowing analysts to focus more energy on investigating the security alerts on the network. Collaboration features in a solution like Linkurious Enterprise also enable them to work together more efficiently. Linkurious meets all security standards for sensitive data and provides all the necessary tools to administer user rights access. Using a graph-based approach also offers many advantages when working with non-technical users and other departments inside the company because of its inherent simplicity.
Want to start exploring your graph data to gain deeper insights, faster? Watch our product demo.
(1) https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
A spotlight on graph technology directly in your inbox.