How to use OSINT for AML investigations: The power of network visualization
Investigators working on money laundering and other financial crime cases have to contend with an increasing amount of complexity, especially as organized groups of criminals are responsible for a higher percentage of financial crime.
Conducting investigations using open source intelligence (OSINT) with the help of network visualization is a powerful way to tackle this complexity. Many investigators are already doing this. In a survey of attendees during our recent webinar on the subject with ACFCS and OpenSanctions, over 75% of fincrime professionals use OSINT in their investigations on a regular basis.
This article explains how open source intelligence works for money laundering and financial crime investigations, with some examples from our latest webinar.
As a financial institution or government agency, your organization only has so much internal data at its disposal. And there’s only so much that data can do to help you accurately assess customer risk.
OSINT is the gathering and analysis of data collected from open, publicly accessible sources. Open data sources can help identify money laundering, fraud, terrorism, and other threats linked to risky entities such as PEPs or sanctioned entities. These publicly available sources include company registries and sanctions lists, but also social media, phone number lookup, geographic information, IP address lookup, search engines, and more.
Regulated institutions need to pay careful attention to information related to customer risk. Ignoring it can result in fines for noncompliance, and those fines can be steep.
OSINT can be a rich source of important information, but it isn’t without its challenges. Let’s take a look at the example of sanctions lists. In theory, sanctions list information is accessible to the public online for free. Anyone can find the OFAC sanctions list by typing that query into Google. However, there are hundreds of potential data sources for sanctions, each in its own format. That might mean different name variations for example. One database may contain only the English transliterations of names in Russian or Arabic, and those transliterations may not match those in other databases.
It’s simple to search for one name in a given sanctions list. But to lead effective investigations, you need to continuously integrate multiple data sources. It can be a complex effort.
In addition to this complexity, ad-hoc OSINT investigations are time consuming and require advanced skills.
Some solutions also focus on a single type of data, such as PEPs, sanctions, or company registries. Or, they focus on a single use case: UBO identification or KYC for example. These types of solutions create silos with data that doesn’t communicate.
Finally, not all organizations have the resources to invest large amounts of money into OSINT analysis on a massive scale.
A knowledge graph unifies relevant data sources into a single network of entities (individual data points) and relationships (the connections between those data points). Within this network, you can see the context surrounding an individual or transaction. The network enables you to analyze and explore internal and external data in the same place.
The knowledge graph acts as the source of truth in an investigation, since it centralizes data. It can:
- Reveal new insights, such as a connection between a client and a bad actor
- Accelerate investigations by reducing the number of tools and tabs an investigator has to open
- Increase confidence: with all sources of information unified in a single network, you can be sure you’re not missing a key piece of information.
A knowledge graph provides relevant context to all investigators. It can also be extended with new tools and data sources. What is the process like to set up a knowledge graph?
The first step is to gather your OSINT sources for sanctions and PEPs. A source like OpenSanctions gives you access to comprehensive sanctions data in one place. Then, create the basis of your financial crime knowledge graph by importing sources into a single database. Entities are represented as nodes and edges. Next, you can integrate other data into your graph: KYC data, transactions, scoring, etc. You can then detect suspicious patterns or conduct investigations. Context enables you to make quick and accurate decisions.
A knowledge graph isn’t as easy to set up as a monolithic solution, but it provides you an enormous amount of flexibility in terms of the tools and data you can incorporate. When building a knowledge graph, it’s best to start small and iterate to improve. For example, you might start with your readily available internal data and then move on to integrate external data sources.
Graph visualization quickly shows you all the information surrounding a given entity, making it easy to understand all the connections to a sanctioned entity or politically exposed person. Here’s an example of how OSINT data uploaded into a graph can help you find the information you need.
You can upload into your graph database OSINT data from sources like OpenSanctions, ICIJ’s Offshore Leaks, and more. You can then define the topical structures as labels in a graph to see how entities relate to one another: politician, sanctioned entity, crime, terrorism, offshore, etc. Once your data is structured, you can start to search and explore.
In this case, let’s take a look at some sanctioned individuals in Russia. Russian laundromats funnel money from different countries into the western banking systems. Rarely will you see a suspicious payment linked directly to a politically exposed or sanctioned person, so you need to seek out intermediary information: beneficial ownership, business relationships, etc. to fill in the gaps between financial crime and decision makers.
We can start by looking at Vladimir Putin, a notorious sanctioned entity. From here, you can run a query to show all Putin’s links to offshore companies, which swiftly returns a large number of results from the Offshore Leaks database. At the same time, you can see entities linked with these offshore companies, such as Igor Putin, Vladimir’s cousin, or the Rotenberg brothers, businessmen and close allies of Putin.
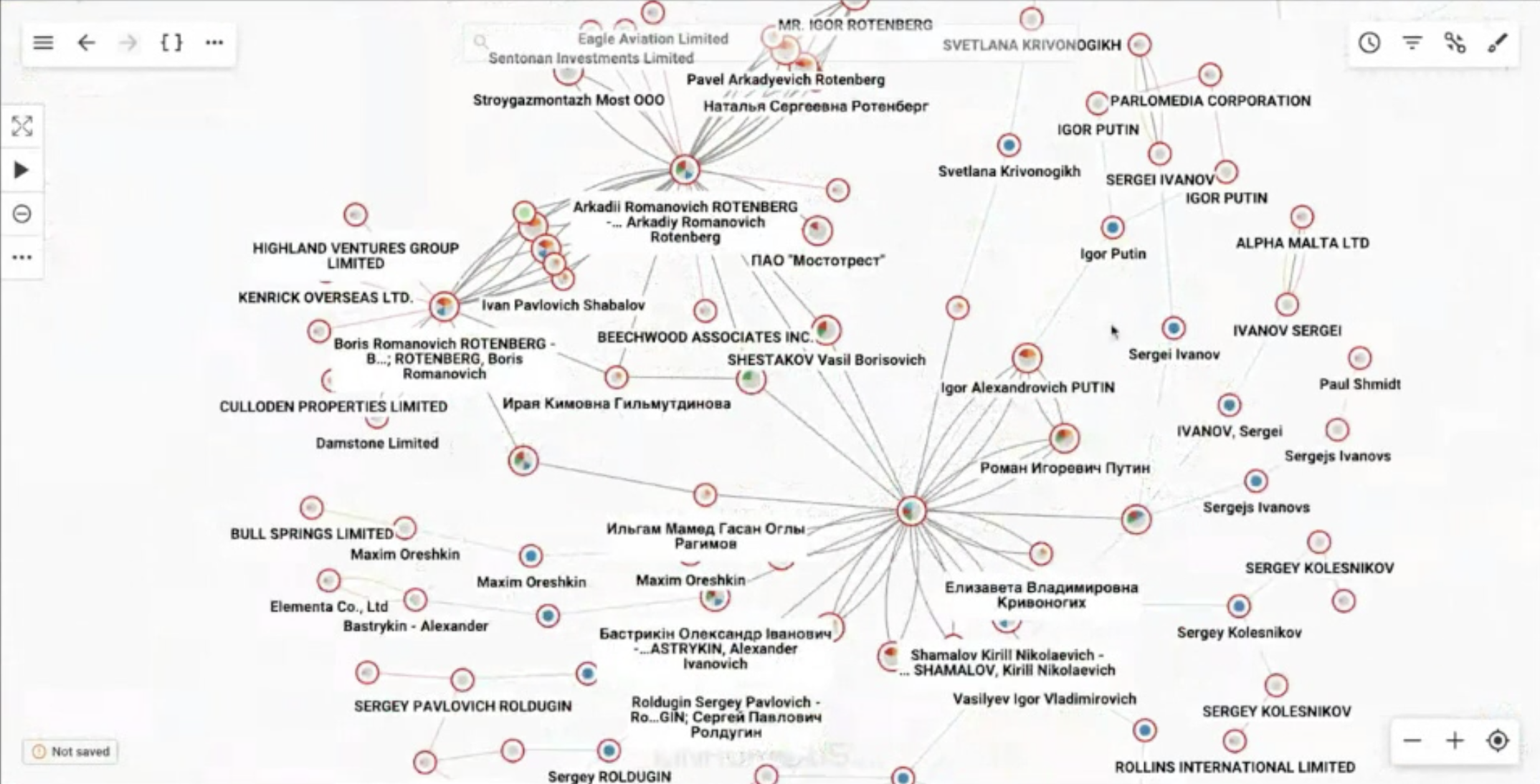
Working in a tool like Linkurious Enterprise, you can set up alerts to search for suspicious patterns in a systematic way. For example, you can configure an alert for connections from a sanctioned entity to a payment. “This is really interesting in the sense that it can let you live out your creativity in imagining all the patterns that would be interesting to an investigator, and then work through the instances of these alerts,” says Friedrich Lindenberg, founder of OpenSanctions.
The connections you can see in the graph represent the beginning of an investigation. The technology is a great tool for building hypotheses that can be further investigated.
With the right techniques, OSINT investigations can be a powerful tool to uncover evidence of money laundering. Watch our webinar, organized in collaboration with ACFCS and OpenSanctions, to learn:
- How to leverage open source information and network visualization to enhance your AML compliance program
- How to get access to consolidated data about sanctions, politically exposed persons or Russian oligarchs
- How to visually navigate complex networks to suspicious connections
A spotlight on graph technology directly in your inbox.



