New account fraud, also called account opening fraud, is a hallmark of several different types of fraud. Banks and other regulated businesses typically have in place robust know your customer (KYC) and customer due diligence (CDD) processes, but sometimes fraudsters manage to break through these defenses. It’s a common way for them to engage in illegal activity while flying under the radar.
This article explains what new account fraud is, three fraud schemes that may be associated with new account fraud, and how graph technology can be your best asset to fight back by helping investigate faster and more efficiently.
New account fraud is when a fraudster successfully opens a new account at a bank or other financial institution for the purpose of committing fraud. Everyone has a new banking or payments account at some point - even multiple new accounts - and most of these are legitimate. But some people open an account with the intention of wrongdoing.
There are multiple ways a fraudster can go about this. They may use their real identity (first-party fraud), a synthetic identity, or a stolen identity (third-party fraud or identity theft). In opening a new account, the fraudster’s goal is to appear legitimate to avoid raising suspicion.
This type of fraud is different from application fraud. In the latter, a fraudster falsifies information to try to appear like a legitimate customer during the application process, but they may not succeed in actually creating a new account.
New account fraud can be understood as a tactic that fraudsters use to commit different kinds of frauds. To illustrate this, let’s take a look at how new account fraud can play a role in three different fraud schemes.
A synthetic identity is a fraudulent identity combining real and fake personal information. It may include a real social security number (SSN) and a fake name, for example. This information together does not belong to any one real person. These fraudsters go through a lot of effort to make their synthetic identities appear real to bypass KYC checks and other screening.
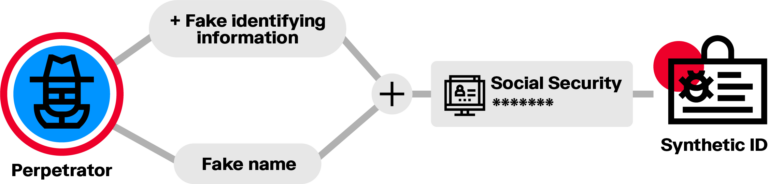
A person opening a new account with a synthetic identity is doing so because they have something to hide. They might use the account to build a good credit score and apply for more and more credit cards or a bank loan. Eventually, the fraudster applies for a maximum amount of credit and then disappears without paying.
There are many ways for an investigator to spot synthetic identity fraud. One red flag is several customers sharing the same information. Another is geographic mismatch, where pieces of personally identifiable information (PII) come from disparate geographic locations.
Credit card fraud refers to any type of fraud committed using a credit card, and there are many ways a person can commit credit card fraud with a new account. Someone could, for example, use a synthetic or stolen identity to open a new account, rack up a lot of charges and then walk away with no intention of reimbursing the credit.
They might also carry out a scheme similar to the one mentioned in the section above. A fraudster might use their credit card to build credit over time and increase their spending limits until they eventually bust out without paying. Spotting this type of fraudster when their account is new - and before they can do any damage - can save a lot of money.
Money muling, also called mule fraud, is when a person or a business moves or transfers ill-gotten funds for someone else. The owner of the funds may be trying to distance themselves from those assets because they have illegal origins: fraud, or drug or human trafficking. The account used by a money mule is called a mule account.
Opening an account for this purpose is fraudulent and illegal. Financial institutions that fail to detect mule accounts can run into serious trouble with regulators, including high fines.
Money mules may or may not be aware that they are participating in illegal activity. And since the “goal” of using a money mule is for criminals to distance themselves from illegal gains, accounts opened for this purpose will often appear legitimate at first. Some red flags for mule accounts are someone transferring maximum amounts of funds shortly after account opening, or mismatch between a person or business’s declared activity and the amount of money in their account.
Graph technology is an analytics method that takes into account not only individual data points but also the relationships between them. In contrast with traditional analytics that rely on tables, graph analytics is built to analyze entire networks of data - and to do it super quickly. Since the clues in a fraud investigation tend to be dispersed across multiple data sources, and because a lot of fraud is perpetuated by organized groups of criminals, graph technology is a powerful asset in getting to the bottom of fraud investigations quickly, and making sure no stone goes unturned.
If a fraudster manages to slip through the cracks of an organization’s lines of defense and open a new account with the intention of wrongdoing, often an alert system will flag suspicious activity on the new account: transferring large amounts of money quickly after opening, for example. Graph technology helps you quickly and easily investigate any red flags to gather evidence as to why a case is fraudulent.
Seeing all connected data at a glance makes graph ideal for catching networks of fraudsters. Analysts can easily see all the data connected to a suspicious account, and all the data connected to each of those data points.
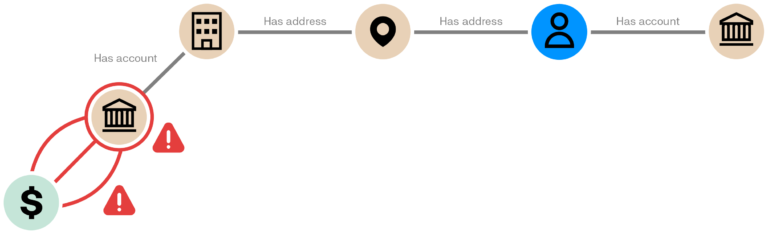
If we take the example of a mule account, graph lets investigators see at a glance where money has been transferred, in what amounts, and which other accounts are associated with the mule account. If the account is part of a bigger money laundering ring, graph will show it without the analyst having to manually chase after information from various sources.
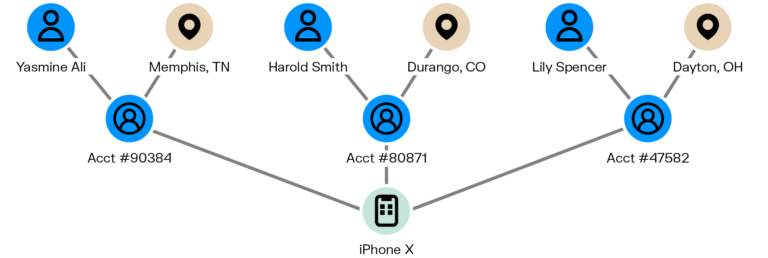
You can also see, for example, if there are devices shared between new accounts. One device linked to five or ten or fifty new accounts is a red flag that the device owner may be using those accounts for credit card fraud or other illegal activity. Each of those accounts should be investigated further. A graph analytics solution can identify a network of suspicious accounts like this very quickly with a simple query.
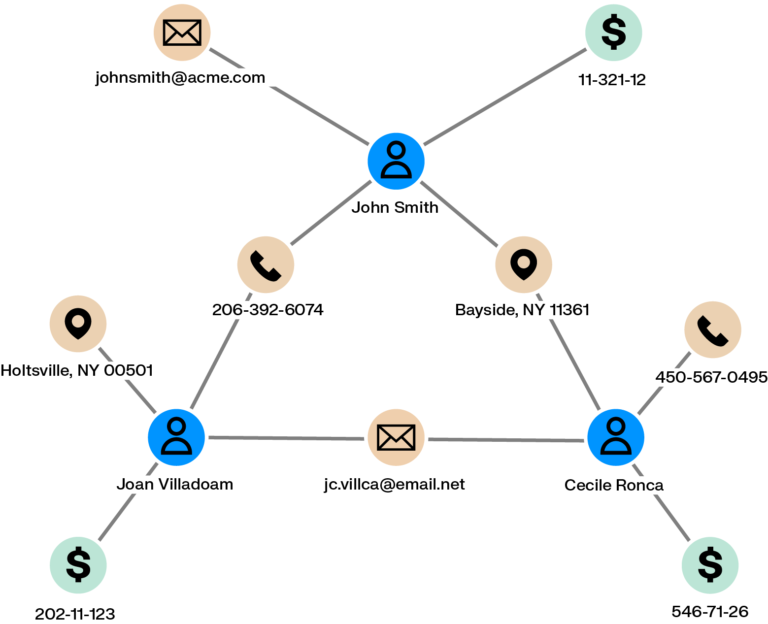
Graph will also quickly show you if a suspicious account shares PII with any other accounts. This is a hallmark of synthetic identity fraud, which can be notoriously difficult to spot using more traditional methods. Seeing the whole context around a case lets you investigate more fraud, faster.
Graph analytics is a powerful tool to detect more fraud and financial crime and to speed up investigations. Learn how graph can help fight back against other types of fraud in our white paper.
A spotlight on graph technology directly in your inbox.


