Fraud is when someone uses deception for unfair or unlawful personal or financial gain. It can be broken down into some broad categories which are useful for better understanding - and fighting - this crime. These categories include first-party and third-party fraud. This article explores third-party fraud by defining what it is and looking at examples of common third-party fraud schemes.
Third-party fraud is when someone’s personal information is used without consent so a third party can illegally or unfairly gain access to resources, credit or products. It’s also known as identity theft, and it’s the most common category of fraud. In third-party fraud, fraudsters hide behind a completely different identity. This differentiates it from first-party fraud, where fraudsters misrepresent who they are by changing details about themself or using a synthetic identity.
To commit this type of fraud, criminals may hack into a person’s account using stolen credentials which may be obtained through phishing or purchased on the dark web. A fraudster might also use someone’s personally identifiable information (PII) to open accounts or to access goods or services.
With more and more services available online, there is an increasing amount of PII available online. Some of this ends up hacked or on the dark web, fueling third-party fraud. Third-party fraud is frequently associated with fraud rings or organized crime, meaning each fraud attack is often part of a wider operation.
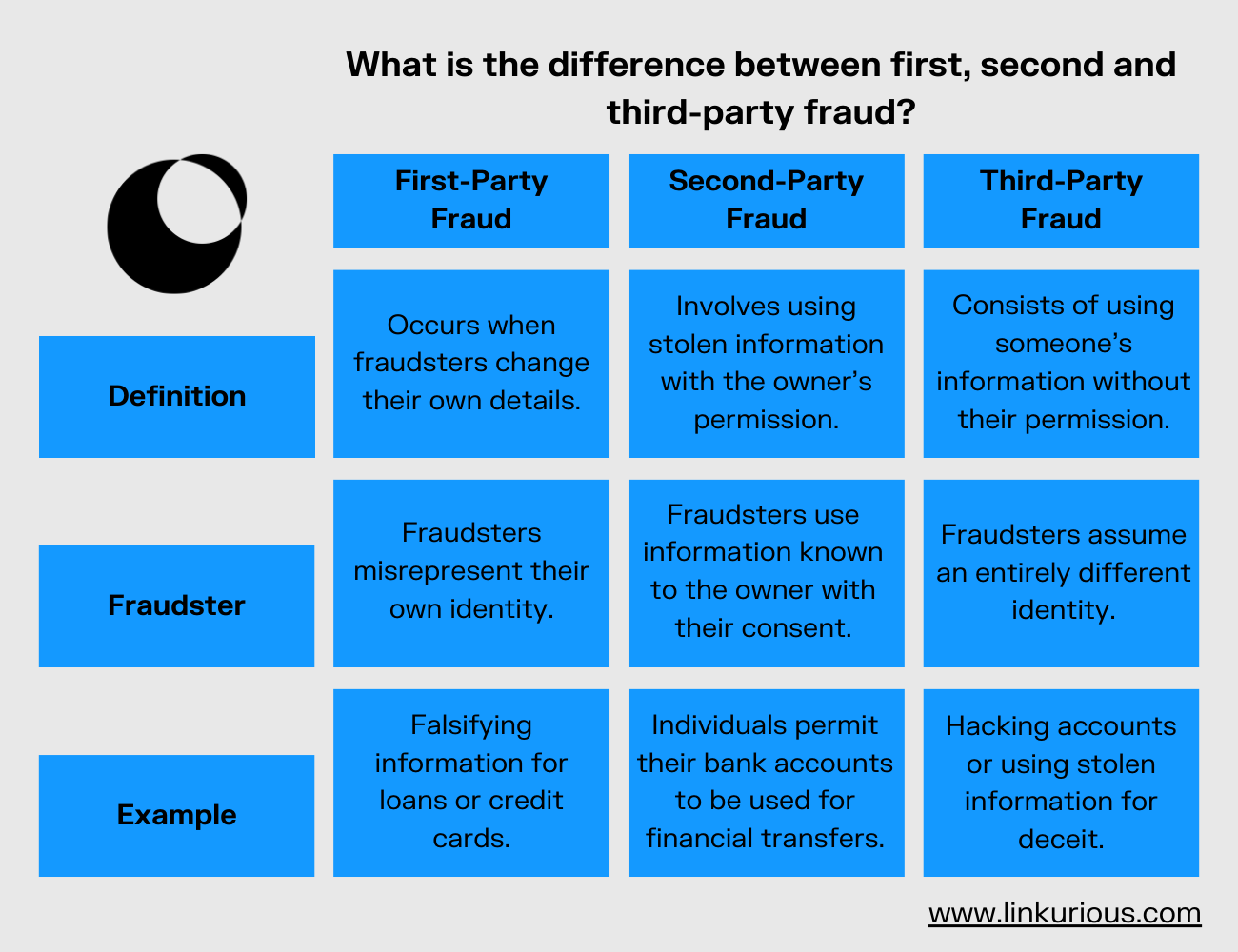
The distinction between these fraud types lies in their methodologies. First-party fraud occurs when individuals deceive by falsifying personal information or using a synthetic identity, often to secure loans or credit lines.
Second-party fraud involves the unauthorized use of acquired credentials or data with the owner's consent. This may entail exploiting familial financial information for illicit transactions. Additionally, second-party fraud includes practices such as money muling, where individuals permit their bank accounts to be used for financial transfers in exchange for nominal compensation.
See the chart below to understand the difference between these categories of fraud.
If all third-party fraud involves using someone else’s identity, there are a number of different schemes that fall into the category of third-party fraud. Here are a few of the most common examples.
Account takeover fraud, or ATO
This is when an unauthorized user gains access to a victim’s account using the account’s login credentials. They then steal assets or personal information, or may sell access to the account itself. This is the most common type of third-party fraud, and can target all kinds of accounts; digital banking, online payments, or even government benefits accounts.
Loan stacking
In this scheme, a fraudster applies for multiple loans under a stolen or false identity and then fails to pay those loans back.
New account fraud or application fraud
A fraudster uses fake or stolen credentials to open a new account. Often they will apply for credit, max it out, and then disappear without paying. They might also use their new account to commit credit card fraud.
Government benefits fraud
A fraudster can use stolen credentials to access or apply for government benefits, defrauding the rightful beneficiary of those assets. This can occur with unemployment benefits, for example.
The consequences of third-party fraud can be devastating for victims: losing money, losing essential government benefits, being locked out of key accounts, or even being mistakenly investigated for fraud after an account takeover. And businesses that fail to prevent third-party fraud can see serious damage to their reputation as they lose customer trust.
Since third-party fraud is often the work of organized criminals, putting into place a robust fraud detection and investigation solution that takes into account the networked nature of threats is essential. A next-generation fraud analytics solution that breaks data out of silos and effectively analyzes relationships and connections can be an important asset to accelerate third-party fraud detection and investigation.

