Internal fraud, also called occupational fraud or insider fraud, poses a threat to organizations of all sizes. The Association of Certified Fraud Examiners estimates that on average organizations lose 5% of their annual revenue to fraud each year, with nearly half of that attributed to internal, employee-driven fraud. And as companies face increasing economic uncertainty, the incentives and pressures that can lead good employees down the path of fraud have never been greater. In fact, over the last several years, incidents of insider fraud have tripled (1).
It’s clear that traditional methods of detection and investigation are no longer sufficient in a context of increasingly sophisticated internal fraud schemes.
This article looks at what internal fraud is and what some common insider fraud schemes are. It also discusses some of the challenges of detecting and investigating this type of fraud - and how new technology is changing the game.
Internal fraud happens when employees in a company use deceptive or illegal conduct to gain money or other benefits. This can include many different types of schemes, for example:
- Insider trading
- Asset misappropriation
- Payroll fraud
- Data theft
- Embezzlement
- Faking records
- Procurement fraud
- Etc.
It's different from fraud perpetrated by outsiders because it hinges on the employee's access to the company's own systems and knowledge. Sometimes insider fraud is carried out in collusion with external accomplices. That was the case in a recent scheme named in a lawsuit by Amazon. The filing revealed how an organized crime group used methods that included working with Amazon employees to process fake refunds in exchange for bribes, enriching the fraudsters.
All together, these schemes are both prevalent and costly:
- 57% of fraud is committed by company insiders or a combination of insiders and outsiders (3).
- Internal threats are becoming more common. There was a 72% increase in insider threat incidents between 2020 and 2021 (4).
- The median internal fraud loss according to the ACFE is $117,000, but of course that can vary widely according to the type of fraud, type of organization, the number of accomplices, and more.
- Overall the financial services industry is the most impacted by internal fraud (4).
Insiders pose the biggest threat to businesses because they possess the knowledge to manipulate their organizations’ systems to their own benefit. Fraudsters familiar with internal systems are also in the best position to hide their misdeeds. They might have access to funds, sensitive data, or restricted systems as part of their job. They also may know company policies around fraud, as well as the hallmarks of fraud their organization looks out for, to better fly under the radar.
Breaches or misuse may therefore go undetected for longer since they can fly under the radar for longer than a hack or break-in at the hands of an outsider would.
Rapid digital transformation and increasingly complex IT systems have also opened up new avenues to fraudsters - both internal and external. When a financial institution or other organization rolls out new tools or technology, it can create unexpected opportunities for bad actors within the company to commit fraud.
More data also equals more assets fraudsters can steal or manipulate to their own advantage.
Finally, both data and defenses are all too often siloed within organizations. Cybersecurity, compliance, AML operations, corporate security, risk management, etc. may all operate separately with little communication or data sharing. This makes it easier for insiders manipulating internal systems to slip through the cracks and evade detection for longer.
With fraud techniques evolving quickly and becoming more sophisticated to outsmart traditional controls, legacy systems based on simple rules don’t have the power and flexibility to keep up. Fraudulent activities continue to fly under the radar.
Organizations need a new generation of analytics tools that can analyze relationships within vast amounts of heterogeneous data. The right tools for the job deliver context-based insights and are able to correlate low signals that point to fraudulent activity when analyzed together.
Graph technology represents a significant advancement in the realm of anti-fraud use cases. At its core, a graph is a way of structuring data as nodes and edges (also known as relationships). Nodes in a graph represent individual data elements such as people, addresses, or transactions, while edges illustrate the connections between these elements, like a person associated with an address or managing a strategic contract.
Unlike traditional data analysis methods that might examine data points in isolation, graph analytics allows for a more interconnected view. This is crucial in fraud detection, since fraudulent activities often involve sophisticated networks and complex relationships and patterns that might not be apparent in a siloed data setup.
By integrating graph technology into their tech stacks, analysts can more efficiently map and visualize these networks, making it easier to spot anomalies and unusual patterns indicative of fraudulent activities. This approach is particularly powerful in detecting sophisticated internal fraud schemes that might span across different departments, locations, or even external entities.
Fraud investigators examining potential cases of internal fraud need to prove complicity in a scheme. Graph can help emphasize the connections between bad actors and fraud incidents to show what’s really going on.
Let’s look at how graph visualization and analytics can be applied to a specific internal fraud use case where it can be a real game changer for detection and investigation efficiency.
For more use cases read our ebook on the subject. You’ll learn how to use graph visualization and analytics to track down internal fraud schemes like:
- Billing schemes
- Asset misappropriation
- False sales and shipping schemes
- Phishing using internal data
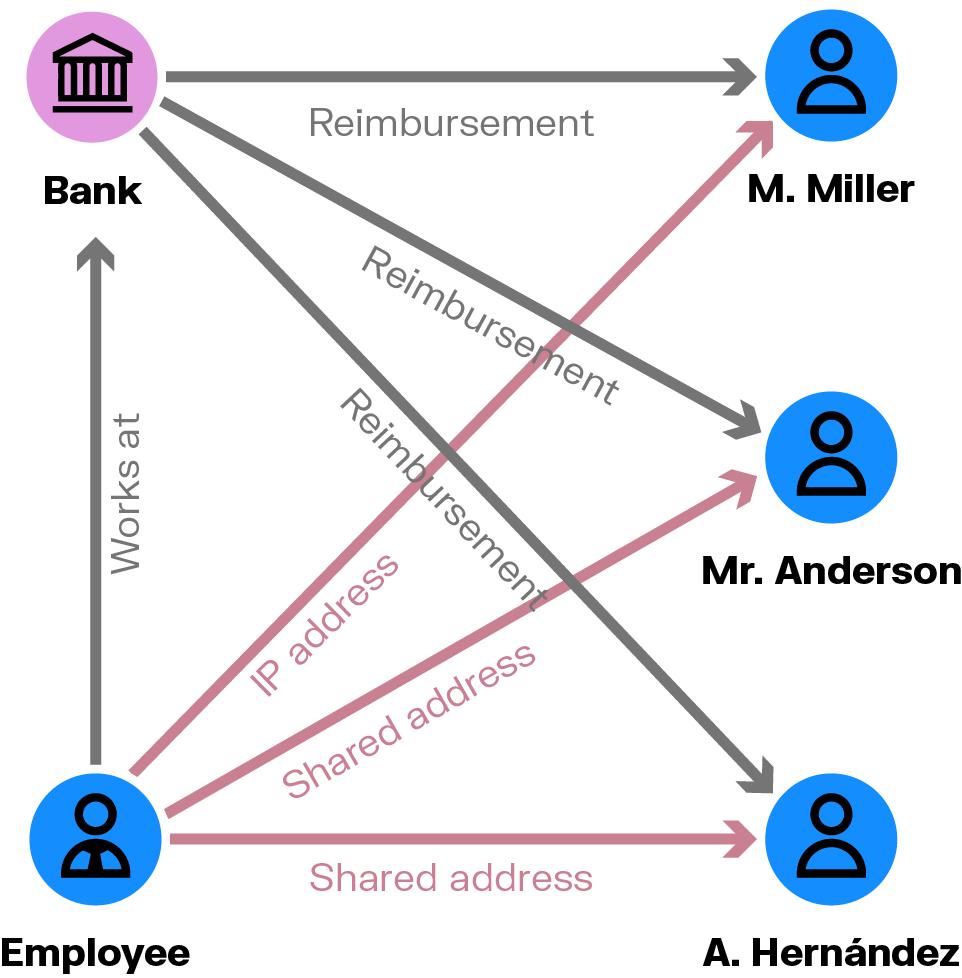
Chargeback fraud is a common problem for banks, and one that poses a big opportunity for collusive insider agents. Someone working at a financial institution may have insider information on how to “game” the system. They might know how to obtain a fraudulent reimbursement, for example, and share that information with friends and family so they can profit.
Graph can show you the social and personal connections that indicate who the individuals taking advantage of the system may be colluding with inside your organization. Does an employee share a home address with someone who has committed fraud? What about their social media connections? Individuals colluding on a chargeback scheme may also share an IP address or devices, such as the smartphone or computer used to access the banking app. A graph will enable you to quickly visualize these kinds of relationships.
There is an urgent need for a paradigm shift in how organizations detect and investigate internal fraud. Traditional methods are proving insufficient in the context of rapid digital transformation and the intricate networks that characterize modern fraud schemes. But advanced technologies like graph analytics offer a more interconnected and dynamic approach to fraud detection.
For a deeper look at leveraging such technology against the threat of internal fraud, download our comprehensive e-book. It expands on the concepts discussed here, offering more detailed insights and real-world examples.
(1) https://www.ibm.com/downloads/cas/LQZ4RONE
(2) https://www.pwc.com/gx/en/forensics/gecs-2020/pdf/global-economic-crime-and-fraud-survey-2020.pdf
(3) https://www2.dtexsystems.com/l/464342/2022-02-07/3lt8pp/464342/16442867128628IH8M/DTEX_Insider_Threat_Report_2022.pdf
A spotlight on graph technology directly in your inbox.



