Cybersecurity threat analysis: building a digital twin with graph to enhance your defenses
Cybersecurity threats are a painful reality for businesses across industries. As organizations the world over have undergone digital transformations quickly and on a large scale, opportunities for bad actors to exploit digital systems have greatly increased. Businesses of all sizes and across industries need to be proactive in protecting their data and systems. The amounts lost to cybersecurity attacks are enormous: the average data breach cost organizations $4.35 million in 2022 (1). Ransomware attacks cost even more. And data breaches are very common. In the same report, 83% of organizations surveyed reported experiencing more than one data breach.
As cybersecurity threats continue to grow in volume and complexity, analysts are tasked with the difficult challenge of managing risk and protecting their organizations. The need for deploying effective and efficient security measures has never been higher. To mitigate risks, analyze threats, and gain greater visibility into their IT environments, more organizations are turning to graph technology.
In this article, we’ll look at how using graph technology can help security teams better perform cybersecurity threat analysis and manage the risks associated with today’s dynamic cyber landscape. We'll also explore how leveraging graph technology to create a digital twin enables security professionals to detect suspicious activity quickly while also providing superior clarity around potential vulnerabilities across all areas of the organization's network infrastructure.
Cybersecurity is a field that is defined by a high level of complexity. Even seemingly basic tasks, like performing an incident analysis, require bringing together many different pieces of information. And with data stored across different tools and sources, it can be difficult to get the kind of holistic view you need to perform deeper analysis and maintain real-time oversight of your IT systems.
The reality on the ground is that compared to cyberattackers, cybersecurity analysts have a tougher job. They need to anticipate every possible attack and spot every vulnerability. Attackers, on the other hand, need only identify a single chink in the armor to break down the defenses and cause harm resulting in financial losses and reputational damage.
There is a diverse array of cybersecurity threats and they are constantly evolving. Security analysts therefore need to be constantly vigilant for new attack patterns.
Some common categories of cybersecurity threats are:
- Social engineering. This involves manipulating people into performing some action against their own interests or to the detriment of the organization they work for. It may involve convincing someone to give out sensitive information via email or over the phone by impersonating a colleague or manager, for example. Phishing is the most common type of social engineering, accounting for over half of reported security breaches according to PwC (2).
- Ransomware. These attacks remove a person or company’s access to their IT systems or data. The attacker will refuse to reinstate access, or may threaten to publish stolen data, if the victim does not pay a ransom. These attacks can result in both financial and reputational damage for the victim, and can have a major societal impact: ransomware attacks on hospitals or healthcare centers, for example, can have serious negative consequences for patients.
- Distributed denial of service (DDoS). Bad actors use hijacked computers that send a large volume of requests to a service, such that it can’t carry out its regular work. The computer systems then no longer function, creating a “denial of service.”
- Risks from third-party vendors. Nearly all companies use third-party vendors so their teams can focus on the core business or services. This can expose organizations to increased cyber risk through those vendors, however.
To fully understand the vulnerabilities in your system and to effectively protect your organization against these types of attacks, you need a full, 360° understanding of your IT ecosystem. Graph technology can get you there.
Graph technology provides a natural way to represent connected data - including complex IT infrastructure. A graph data structure consists of nodes (individual data points) and edges (the connections between those data points). Together they form an interconnected network of data that makes it easy to spot patterns and anomalies, understand interdependencies, and more.
Graph databases, where graph data is stored, are a good fit to enhance your cybersecurity arsenal since they can integrate many data sources and incorporate large data volumes. Given that many organizations have dozens of security tools deployed, it’s essential to be able to de-silo that data. By bringing everything together into one system, connecting the dots between various signals, and gaining contextual information around those signals, it becomes easier to proactively spot suspicious patterns of behavior or weaknesses in certain defenses. It also simplifies performing complex forensic analysis post-attack, which can involve bringing together vast amounts of data to understand the what and the how of the attack in order to take strong preventative measures for future security.
And, by applying a graph visualization solution on top of your database, tracking down patterns and anomalies becomes intuitive, and sharing reports and findings is much easier.
There are many ways to apply graph technology to cybersecurity threat analysis and risk management. We’re going to take a look at one technique that some organizations use: building a digital twin knowledge graph of a part of or your entire IT and security ecosystem. A digital twin can be used by cybersecurity analysts to query in order to locate weak points, identify key risks and dependencies, and perform impact analysis in case of an attack. It can also be used to build detection models for malicious activities,
The data you bring into your digital twin may include:
- Connected devices
- User access events
- Application resources usage
- Service health
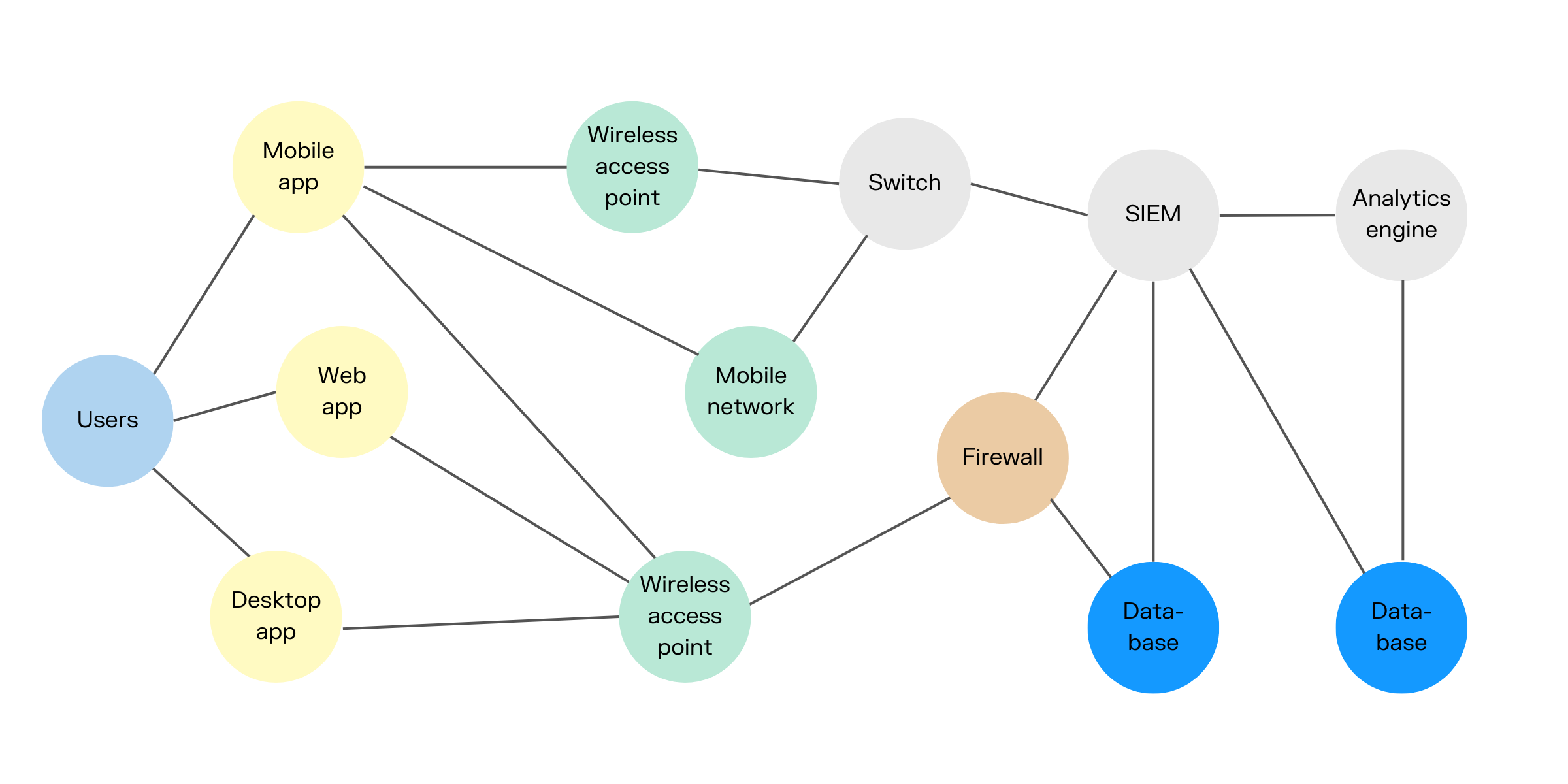
Once you bring data into your cybersecurity digital twin, it will show information like which systems are open to the internet, who your users are and what groups they belong to, user permissions, which systems are connected to which others, etc.
There are many different actions you can take on your cybersecurity digital twin. Let’s look at a few examples.
Attack paths look at things from the perspective of a potential attacker, examining the path of a possible multistage attack and the vulnerabilities at each stage. This goes beyond looking at static vulnerabilities; it’s about understanding how an attacker could use those vulnerabilities as part of a more complex attack.
This type of cybersecurity threat analysis looks at the different paths an attacker may take through your infrastructure. Using graph visualization for this type of analysis is almost indispensable. A visualization makes it fast and intuitive to understand at a glance what different attack paths might be.
Certain elements may increase the likelihood of your organization coming under attack. Mentions in the news may place you on attackers’ radar, for instance. When new loopholes and vulnerabilities are discovered, attackers also won’t hesitate to use them.
It’s possible to ingest data about such vulnerabilities into your graph. Using your digital twin, you can build reports and create alerts about potential security impact, and make proactive changes to your system based on those findings.
No cybersecurity system is perfect, so it’s virtually impossible to prevent all breaches. In cases where an attacker managed to get around your defenses, detecting the attack as quickly as possible will help mitigate damages. Graph can help with this.
Using a tool like alerts in Linkurious Enterprise, you can scan at regular intervals for suspicious patterns of behavior that might indicate the beginning of a cybersecurity attack or other criminal activities that could target your systems or your clients. There are many different types of behavior you can monitor. You can receive an alert if the same IP address has made multiple login attempts, or if you’re receiving many login attempts from an unusual geographic location.
You can set up alerts to flag attack fingerprints that have been seen before. This will let you know if a bad actor (maybe the same one) is following a similar attack strategy.
You can also look for an unexplained traffic surge in your network, which could be the beginning of a DDoS attack.
As organizations continue to strive to secure their environments against the most sophisticated cybersecurity threats, it’s essential to deploy solutions that are up to the task. Graph technology provides valuable insights into the underlying networks of IT infrastructure, giving teams greater visibility to better manage risk.
Linkurious Enterprise provides a graph visualization and analytics solution with a comprehensive set of tools including powerful alerting and advanced collaboration to help you quickly and efficiently gain actionable insights from your IT environments. Try it out today to see how Linkurious Enterprise can help you take a proactive approach in defending your network against threats.
(1) https://www.ibm.com/downloads/cas/3R8N1DZJ
(2) https://www.pwc.co.uk/forensic-services/assets/pwc-global-economic-crime-survey-2018-uk.pdf
A spotlight on graph technology directly in your inbox.