Account takeover fraud - also called ATO fraud or account compromise - has been emerging as a major challenge for all kinds of organizations. We have online accounts for everything today: financial services, shopping, travel - you name it. These many accounts create tempting opportunities for unscrupulous criminals. Account takeover attacks are increasingly common. A study by Aité Group in 2020 showed that 38% of those surveyed had experienced account takeover fraud within the past two years (1).
Because fraudsters use the accounts of legitimate users for illicit gain in this type of fraud attack, detecting and investigating it can be especially challenging even as it causes a great deal of damage. This article explores what defines account takeover, some of the most common ATO schemes, and how graph analytics can help you more quickly and efficiently detect and investigate account takeover fraud.
Account takeover fraud is when an unauthorized user gains access to a victim’s account using the account’s login credentials. They then steal assets or personal information, or may even sell access to the account itself. These fraudsters sometimes change personal information such as the email address or phone number, once they are in to prevent the legitimate account holder from logging back in.
Many types of accounts may be the target of account takeover. Digital banking or online payments accounts are common targets. So are online shopping accounts, which can be used to make fraudulent orders. Fraudsters may also take over government benefits accounts to steal unemployment benefits, for example.
ATO attacks can be costly for businesses and customers, and can also do a number on a company’s reputation. If account takeover is handled in a way that is unsatisfactory, customers may leave. And on the account-holder’s side, the consequences can be devastating: lost money, lost government benefits, being locked out of key accounts, or even mistakenly investigated for fraud themselves.
With digital transformation in full swing, there are many ways a fraudster can access an online account. They might use hacking or malware to steal passwords for example. Account credentials are also readily available for purchase on the dark web. This information is easy to obtain. Online fraud has grown so much that some criminals have set up fraud-as-a-service businesses, selling account information and other private data to help others commit fraud.
Furthermore, with the average person having over 100 online accounts - many of which may share at least some identification information or passwords - it can be easy for fraudsters to access several accounts with the same credentials.
Here are some of the most common examples of account takeover schemes.
With credential stuffing, a fraudster profits from the fact that many passwords and other identifying information may be reused across several accounts. Using software or a script, they test the stolen account information they have procured across hundreds of different websites. If they are lucky - and the victim unlucky - they can take over multiple accounts with just a small set of passwords and personal information. It’s like taking a set of keys and trying them at multiple doors until finding the ones that unlock.
Phishing imitates a real person or legitimate business in order to steal identity information, passwords, and assets. It exploits human psychology and people’s natural tendency to trust other people.
Malware (“malicious software”) gets secretly installed on someone’s device - sometimes using phishing - to illicitly access accounts and funds. Phishing and malware are generally costly for fraudsters in terms of time and effort, so these tactics are most commonly used for attacks on accounts where the potential for payout is big, such as financial services and payment accounts.
A Man-in-the-Middle (MitM) attack is a type of social engineering where the attacker secretly intercepts and even alters the communication between two parties who believe they are directly communicating with each other. The attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
The attacker can not only eavesdrop on the conversation but also manipulate the content, enabling them to obtain account information, for example.
SIM card swapping is another tactic fraudsters use to hack into online banking accounts. Mobile providers will send a new SIM card to customers who buy new devices that are not compatible with their existing SIM format. Using social engineering, a fraudster will call a mobile company and convince them to send a new SIM. Now they have access to the victim’s phone number. If the phone number is used for authentication to access online banking or make payments, the fraudster now has free reign over their victim’s assets.
ATO fraud detection is particularly difficult because these fraudsters mimic normal login behavior. They are also able to hide behind the good behavior of the legitimate account holder. It’s not easy to spot fraudulent activity in an account that may have years of positive history, especially when fraudsters go to great lengths to avoid raising red flags.
Monitoring low signals to detect signs of abnormal behavior is therefore key to catching account takeover fraud.
Graph analytics, which is built to analyze and visualize networks and connections within your data, is one of the best tools to effectively fight back against ATO fraud. In a graph database, data is structured as nodes (individual data points) and edges - also called relationships - which carry information on how two nodes are connected.
An investigation tool powered by graph analytics and visualization like Linkurious Enterprise gathers data into one place, analyzes connections, and surfaces even low signals to detect cases of fraud. Investigating possible ATO attacks is faster and easier. Linkurious Enterprise clients like Pole Emploi, the French unemployment agency, use the solution to proactively detect large-scale account takeovers to prevent fraudsters from stealing unemployment benefits. BforBank has also used Linkurious Enterprise to improve fraud detection and reduce investigation time.
How exactly does graph technology help in investigating account takeover fraud?
Device use is one element analysts look at carefully in ATO investigations. A single mobile phone that has access to 50 different accounts on the same platform, such as PayPal, is a major red flag. Often a fraud network will use just a few devices to access many different accounts. One of the challenges analysts face is determining which device belongs to the legitimate customer.
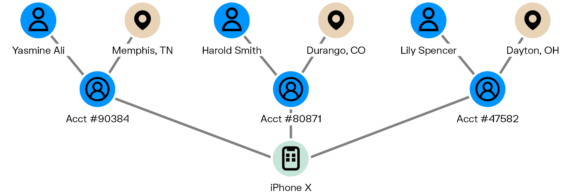
When investigating using graph, there’s no need to open each user’s account information for the investigator to obtain the information she needs. Graph enables you to easily see if and how accounts are linked to one another via devices, transactions, etc. It gives a clear picture of good accounts, bad accounts, and the exit accounts fraudsters are using to offload funds.
Let’s look at one example of an ATO investigation scenario, and the role graph can play. A customer might call their bank or an online payment service to report that their account has been hacked and there are unauthorized charges on their account. The investigator needs to determine if the account truly has been hacked. The investigator would then look at how the account was typically accessed. In this case, the customer has always logged in using an iPhone X, frequently from an IP address in Patterson, New Jersey. The allegedly fraudulent transactions were done using a laptop with an IP address in a different state. Using graph visualization, the investigator also looks to see if that laptop can access other accounts, all of which are located in states all around the country. She sees it has access to a total of 43 accounts. The investigator can also see in the graph that the fraudster has been sending funds to an exit account, and then to ApplePay.
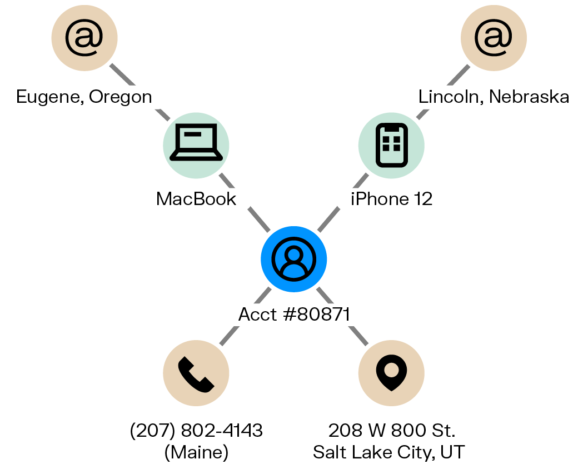
In a few clicks, a graph solution like Linkurious Enterprise lets you see the laptop and any linked devices, and all linked accounts. An exit account, which would be newly opened and only withdrawing money would also be clearly visible in a graph. To prevent further fraud from occurring, an investigator could also quickly block the email address used to open the exit account and any devices used to commit fraud.
Account takeover fraud can do major harm to both individual customers and to organizations ranging from financial institutions and other businesses to government agencies. But graph technology is a promising tool to help detect ATO attacks faster and more efficiently. By enabling analysts to explore the connections between users, devices, geographical locations, transactions, and more, graph analytics makes it easier to flag suspicious activity and speeds up account takeover investigations.
A spotlight on graph technology directly in your inbox.


