Unmasking money mule fraud: Investigate mule networks in minutes instead of days
Ever feel like your traditional anti-fraud tools are stuck in the past while criminals are rewriting the rules? With the prevalence of money mule fraud, it can often seem like this - but there is a better way.
In this article, we’re diving into the world of money mule fraud, looking into how these schemes work and why they are such a challenge for fraud fighters. You’ll understand how criminals often manipulate unaware individuals, how traditional fraud detection methods fall short, and how new technologies like graph analytics can be a game-changing tool in exploring hidden connections and detecting these complex networks. Explore the different types of money mules, discover innovative methods to track illicit funds, and find out how to stay ahead of advanced financial crime schemes.
Money mules aren’t your typical villains. They’re often unsuspecting individuals who become pawns in a larger financial scheme. A money mule is someone who transfers or moves illegally acquired money on behalf of others. Criminals use them to quickly move their illicit proceeds across different bank accounts and sometimes to foreign jurisdictions, effectively distancing the funds from the true beneficiary.
Fighting money mule networks isn’t just about stopping a few bad transactions, it’s about cutting off a key source of money for organized crime. These networks are behind everything from investment scams and counterfeit bank cards to account takeover fraud. Some criminals have even turned money laundering into a full business, offering "money mule as a service" to other criminal groups.

Recent investigations reveal the alarming scale of this problem. An operation by Europol uncovered almost 10,000 money mules in just three months, a discovery linked to roughly $100 million in fraudulent transactions. Even more concerning, a FraudSMART study shows that one-third of young adults between 18-24 would consider using their bank account to transfer illegal funds, highlighting the potential recruitment pool for these criminal networks.
The increase in online scams and social engineering tactics has fueled the growth of money mule schemes. In 2023, Americans lost approximately $1.14 billion to romance scams, nearly doubling the previous year's losses. These scams are a classic example of online fraud and social engineering in action, with criminals using fake online identities to build trust and deceive victims into transferring illicit funds. In many cases, this manipulation turns innocent people into money mules, who unknowingly move illicit funds, making it harder to trace the criminal activities.
Not all money mules are the same, but they all need to be stopped. To a financial institution, a money mule is a money mule, regardless of how much they know about their role in financial fraud.
But in reality, money mules have different levels of awareness and intent, making detection an even more complex challenge. Here’s a closer look at the different types of money mules:
- Unwitting money mules: These individuals have no idea they’re part of a criminal scheme. They believe they’re helping an employer, a friend, or even a romantic partner by transferring money.
- Witting money mules: They might not fully understand the depth of their involvement, but they’ve ignored enough red flags to know something isn’t right. Whether it’s a “too good to be true” job offer or a request that feels off, they choose to look the other way and go along with it for personal gains.
- Complicit money mules: These are the ones who know exactly what they’re doing, and they do it willingly. Some are just getting started, while others are seasoned fraudsters running entire money mule operations.
To effectively stop mule fraud, financial institutions need to go beyond just flagging suspicious transactions. Each type of money mule behaves differently, and detection strategies need to be adapted. Behavioral and contextual monitoring and finely tuned alert systems can help uncover both the clueless and the complicit.
Mule fraud is particularly difficult to detect because fraudsters are specialists in how to avoid raising red flags. Trusted accounts with clean transaction histories are less likely to trigger suspicion, allowing criminals to move funds through legitimate channels without immediate detection. Instead of large, high-risk transfers, they use small, frequent transactions designed to bypass traditional fraud detection systems.
This makes it significantly harder for financial institutions and law enforcement to distinguish between normal banking activity and illegal money transfers, allowing criminal networks to stay ahead, escape from detection, and sustain their operations.
At the same time, with regulations tightening, financial institutions face increased pressure to stay ahead of these sophisticated schemes.
Traditional financial crime analytics often focus on detecting outliers, transactions that deviate from the norm. However, financial crime rings know how to act “normal” to avoid detection.
Conventional fraud detection systems struggle to combat money mule networks effectively, as the criminal strategies exploit the weaknesses in those monitoring approaches. Most systems are designed to flag high-value, isolated transactions, yet mule account schemes often operate through numerous low-value transfers that often fly under the radar.
Criminals further complicate detection by exploiting cross-border operations and advanced anonymity techniques, creating complex financial paths that standard anti-fraud systems have difficulties in tracing. This gap in detection shows the urgent need for more sophisticated solutions to identify and uncover the full extent of these complex criminal networks.
Graph analytics is like a magnifying glass for illicit activities, showing the hidden links that other methods miss. Graph analytics is built on a structure of nodes and edges, where each node represents an entity, such as a person, account, or transaction, and each edge defines the relationship between them. This approach enables analysts to see beyond isolated transactions and understand how money moves through connected accounts, connecting all the dots in a more intuitive, and more visual, way.
One of the graph analytics’ greatest strengths is its ability to simplify the extremely complex web of connections between digital fingerprints, financial transactions, and locations, giving investigators the full picture in a way that traditional methods can’t provide. It's like going from looking at a blurry snapshot to seeing the whole story unfold in real time.
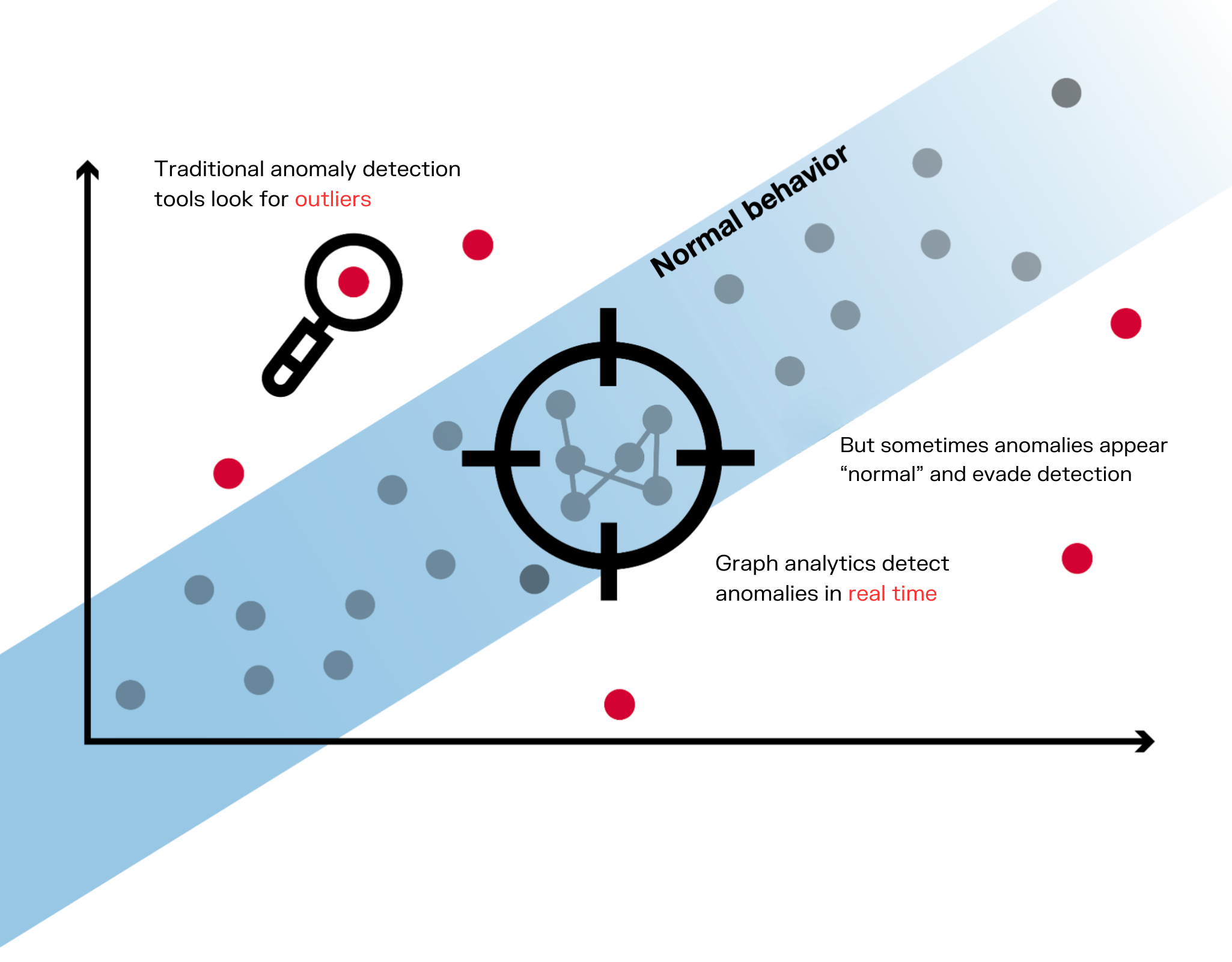
Graph algorithms help investigators see important patterns and major actors within transaction networks. By using different types of graph analysis, investigators can identify suspicious connections, predict potential links, and detect emerging fraud patterns more effectively.
Some of the key graph analysis techniques include:
- Pathfinding: Traces indirect connections between entities.
- Link prediction: Evaluates the chances of two entities being connected, even if a direct link has not yet been detected.
- Similarity analysis: Compares transaction patterns to detect criminal networks with structures that look like previously known fraud schemes.
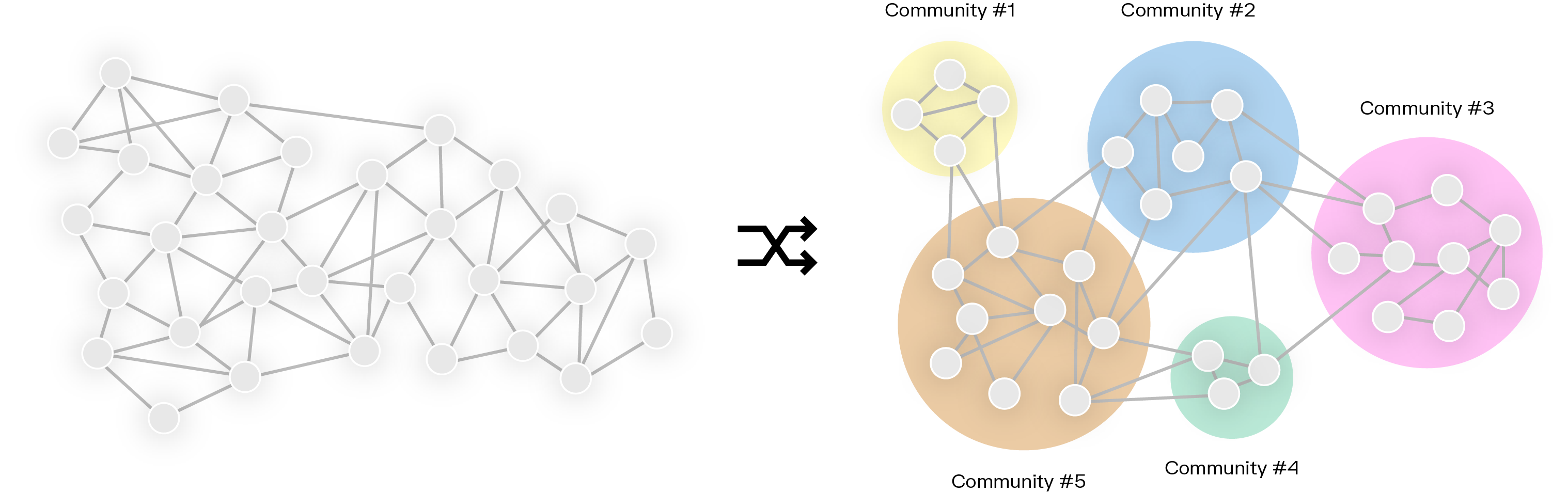
- Community detection: Finds clusters of accounts that are closely linked, identifying hidden networks of money mules. Community detection algorithms help find clusters of nodes in a graph that are closely linked with one another.
- Centrality analysis: Identifies key players in a network by measuring their influence and connectivity. Centrality algorithms pinpoint the key nodes in a graph by analyzing their connectivity and influence.
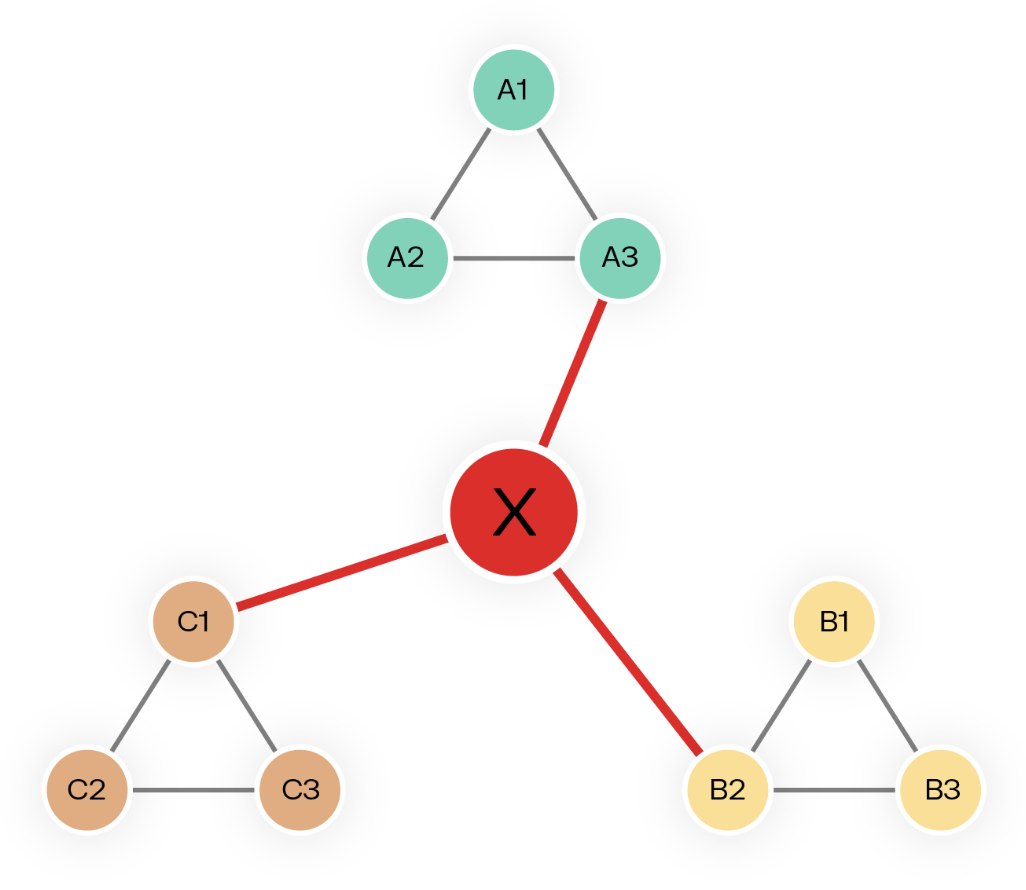
By applying these methods, investigators can have a better view of how illicit networks operate and take faster action to stop financial crime.
Graph analytics is proving to be a powerful tool in money mule fraud investigations. Platforms like Linkurious Enterprise allow analysts to visualize relationships between seemingly unrelated accounts, revealing coordinated clusters that may be active money mule networks. Organizations using Linkurious Enterprise have seen:
- Increase in detection: Spotting up to 20% more suspicious activity by using graph technology to simplify how they visualize data connections.
- Faster response time: Implementing Linkurious Enterprise in their anti-fraud toolkit also reduced alert triage time by 30%, with investigations up to 10x faster.
- 360° tracking: Monitoring of money flows from multiple angles to catch hidden money mule schemes.
- Quick identification of key actors: Easier analysis of transaction patterns to find central figures in fraudulent operations.
These capabilities enable fraud teams to make smarter, faster decisions, disrupt money mule operations more effectively, and ultimately secure financial systems against sophisticated criminal networks.
Want to see how financial crime investigators unmask mule accounts? Our demo takes you through an investigator’s journey from initial alert to final case resolution, showing how graph analytics can uncover an entire money mule operation in minutes rather than days.
In this demo, we showcase how Linkurious Enterprise transforms raw financial data into actionable intelligence. The investigation reveals:
- A complex network of interconnected accounts
- Hidden patterns in transaction flows
- Shared digital fingerprints between seemingly unrelated people
- Real-time timeline analysis of fund movements
Watch our detailed demo below:
Learn more about using graph analytics and visualization to combat money mules: watch our webinar replay.
Money mules are a dynamic and challenging aspect of modern financial crime, but with graph analytics, financial institutions now have a powerful ally in the fight to stop these criminals in their tracks. By revealing hidden connections and contextual relationships, this approach helps financial institutions stay ahead of complex threats and protect the integrity of their financial system.
Graph analytics and visualization is a powerful solution for detecting not only synthetic identity fraud, but many other types of complex fraud. See how graph analytics can speed up fraud investigations and improve fraud detection in our in-depth ebook.

A spotlight on graph technology directly in your inbox.

